It will. It’s the whole point of the process as if you had access to the device yourself you’d be able to get a 2FA code sent to it and be able to reset the password. The account recovery process is for when you don’t have the password and don’t have access to the trusted device.I did read it. Read it yourself. It wont help you if someone changed your password and passcode on your trusted device.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Apple Responds to Report About Thieves Spying on iPhone Passcodes to 'Steal Your Entire Digital Life'
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Prove that.It will. It’s the whole point of the process as if you had access to the device yourself you’d be able to get a 2FA code sent to it and be able to reset the password. The account recovery process is for when you don’t have the password and don’t have access to the trusted device.
No need, it’s just how it works described right on Apple’s own website 😀Prove that.
I wish you were right, but I still don't believe it, and there's nothing in the document you posted that gives me any confidence in what you say if someone had changed your passwords and passcodes.No need, it’s just how it works described right on Apple’s own website 😀
It’s the very first paragraph 😀I wish you were right, but I still don't believe it, and there's nothing in the document you posted that gives me any confidence in what you say if someone had changed your passwords and passcodes.
That's definitely not true.It’s the very first paragraph 😀
It’s the very first paragraph 😀
And until you get through that procedure an attacker can wipe your whole iCloud data and remote wipe devices which you have signed into the same Apple ID. All that only by knowing a 6 digit passcode.
Maybe most Apple customers are fine with that risk. I would still appreciate it if there was a way to make my Apple ID more secure.
Also, the procedure you linked to is for users who forgot their password or don't have access to 2F authentication. With a passocode and a device an atacker can just change all the emails and phone numbers associated with your account.
Last edited:
You can go through the same iCloud account recovery with Apple.
How to use account recovery when you can’t reset your Apple Account password – Apple Support (UK)
If you use two-factor authentication and can’t sign in or reset your password, you can regain access after an account recovery waiting period.support.apple.com
This doesn’t work if someone has compromised your account and is actively thwarting your efforts.
Did Apple do anything to address this issue in iOS 17?
Interesting tests on this subject are reported here and here. But, at present, it appears that a thief in possession of an iPhone and its passcode still has the ability to change a user's Apple ID in iOS 17, thereby permanently locking access to the Apple account by the user.
CC: @Mike Boreham, @KaliYoni
Interesting tests on this subject are reported here and here. But, at present, it appears that a thief in possession of an iPhone and its passcode still has the ability to change a user's Apple ID in iOS 17, thereby permanently locking access to the Apple account by the user.
CC: @Mike Boreham, @KaliYoni
In both those threads I reported that iOS 17 had fixed the problem.
However @citivolus has reported in the same MR thread, it hasn't. He used a slightly different sequence which resulted in still being able to change Apple ID password with just the phone passcode, even if a 28 digit Recovery Key has been set and even if Screen Time has been set.
I have update both the threads you linked.
Apple should make it so that if you have a security key set as your 2FA then iOS will require that key in order to change the password.
They should definitely have some additional layer of security, even if only as an option.
Apple’s iCloud Keychain is very handy for me but I’ve started using 1Password in addition for a smaller number of accounts which are particularly important.
Apple’s iCloud Keychain is very handy for me but I’ve started using 1Password in addition for a smaller number of accounts which are particularly important.
iOS 17.1 is anticipated to include updates related to Screen Time (see here). Perhaps those updates may also address the current flaw that allows a malicious person in possession of an iPhone and its passcode to bypass Screen Time restrictions and reset a user's Apple ID password? Time will tell....
I understand the potential need for some users to choose lower security. But seems so dead easy to add a layer option that will not allow iPhone passcode to be the key to all things including Apple ID change. I thought physical keys were answer …but clearly resettable with magic iPhone passcode.
Sorry if this is known ….but why is apple sticking so firmly to the all powerful iPhone pin when it is a huge and life altering risk…. With seemingly easy mitigant.
Is it embedded too deeply in core infrastructure ? Is screen time the intended fix but broken for now ? And do we think apple has intention to fix? By their recent response it seems not.
Sorry if this is known ….but why is apple sticking so firmly to the all powerful iPhone pin when it is a huge and life altering risk…. With seemingly easy mitigant.
Is it embedded too deeply in core infrastructure ? Is screen time the intended fix but broken for now ? And do we think apple has intention to fix? By their recent response it seems not.
It’s only a life altering risk if your device passcode falls into the wrong hands. That’s why the solution is to be vigilant when inputting it in a public place as opposed to a mess of different passcodes enforced by Apple.I understand the potential need for some users to choose lower security. But seems so dead easy to add a layer option that will not allow iPhone passcode to be the key to all things including Apple ID change. I thought physical keys were answer …but clearly resettable with magic iPhone passcode.
Sorry if this is known ….but why is apple sticking so firmly to the all powerful iPhone pin when it is a huge and life altering risk…. With seemingly easy mitigant.
Is it embedded too deeply in core infrastructure ? Is screen time the intended fix but broken for now ? And do we think apple has intention to fix? By their recent response it seems not.
This is why you don’t see Apple doing anything about it as there’s nothing to fix; the fix is with the device user themselves.
I disagree as do many others. It is not the fault of users that a single code no matter how complex allows access and lockout of all apple data forever. I posted as a work colleague was taken at knifepoint and had to provide passcode. And hence an unnecessarily huge impact. From a phone passcode. Is it user error if daughter or wife held up? How about a phone phone code is limited to accessing the phone. And allowing user to decide how far reaching that code is. Easy. Your answer is not helpful.
But that’s so unlikely to happen vs the more common scenario of people being locked out because they now have multiple device passcodes.I disagree as do many others. It is not the fault of users that a single code no matter how complex allows access and lockout of all apple data forever. I posted as a work colleague was taken at knifepoint and had to provide passcode. And hence an unnecessarily huge impact. From a phone passcode. Is it user error if daughter or wife held up? How about a phone phone code is limited to accessing the phone. And allowing user to decide how far reaching that code is. Easy. Your answer is not helpful.
But one can choose any number of alternate resets that are simply outside that device. Other apple device, hard key, separate passcode. And any could be optional layer. Self contained all powerful iPhone code … and sms or verification to same device is just not rational.But that’s so unlikely to happen vs the more common scenario of people being locked out because they now have multiple device passcodes.
All of which add complexity and heighten the risk of users being locked out of their devices/accounts. No I think on balance the current approach is best so that most users have a good balance of security and convenience.But one can choose any number of alternate resets that are simply outside that device. Other apple device, hard key, separate passcode. And any could be optional layer. Self contained all powerful iPhone code … and sms or verification to same device is just not rational.
Let's roll!
Or, at least, keep an eye out:
 www.macrumors.com
www.macrumors.com
I am on 17.2 and I know my iPhone 14 Pro already requires Face ID from me to view passwords/passkeys in the keychain. However, there are lots of other features which are clearly new and sound promising.
Or, at least, keep an eye out:

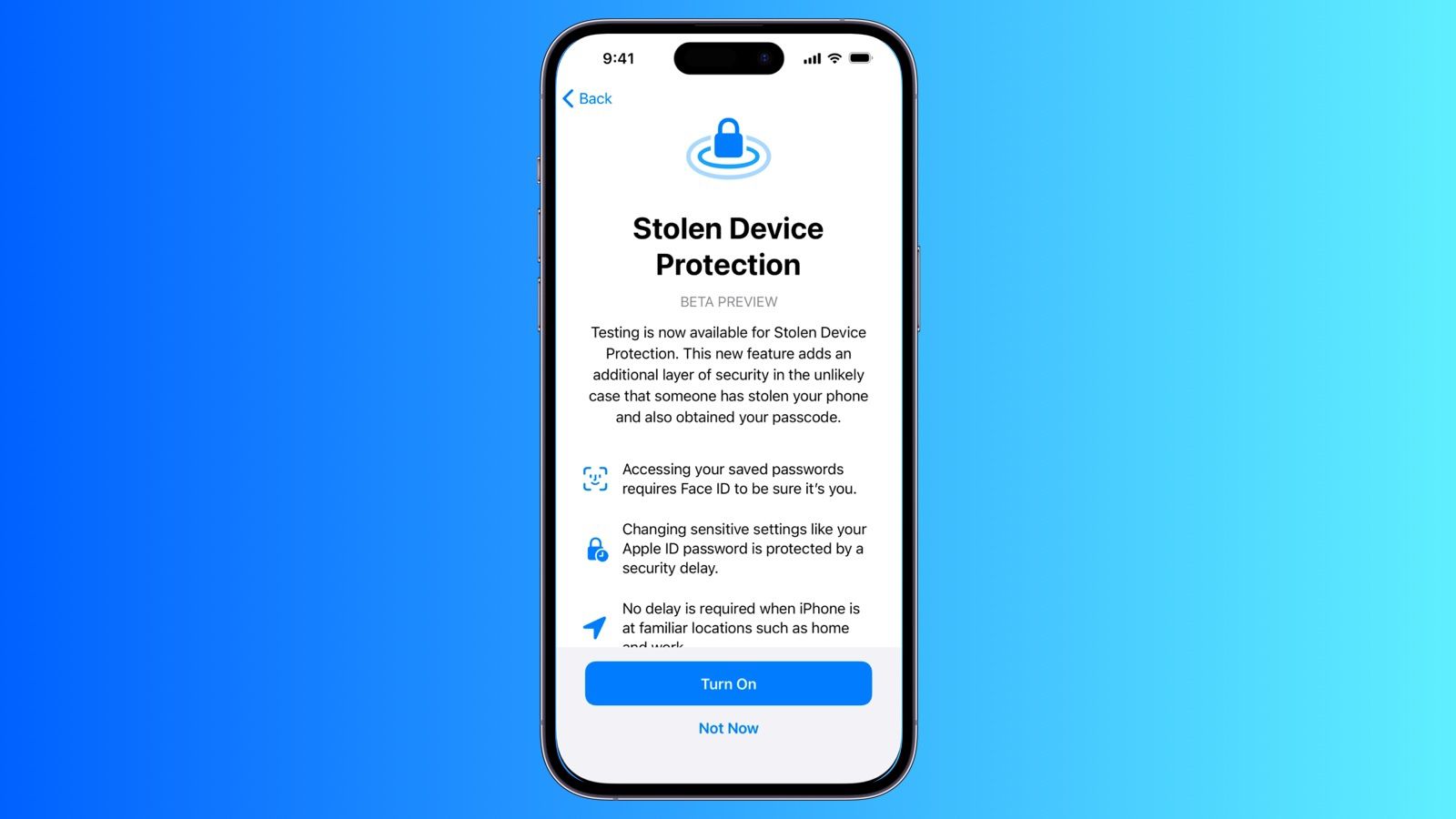
iOS 17.3 Beta Adds New Stolen Device Protection Feature to iPhone
The first iOS 17.3 beta rolling out to developers today includes a new "Stolen Device Protection" feature that is designed to add an additional layer of security in the event someone has stolen your iPhone and also obtained the device's passcode.
When Stolen Device Protection is turned on, iPhone users are required to authenticate with Face ID or Touch ID for additional actions, including viewing passwords or passkeys stored in iCloud Keychain, applying for a new Apple Card, turning off Lost Mode, erasing all content and settings, using payment methods saved in Safari, and more. This extra step ensures that a thief cannot perform these actions with the iPhone's passcode alone.
I am on 17.2 and I know my iPhone 14 Pro already requires Face ID from me to view passwords/passkeys in the keychain. However, there are lots of other features which are clearly new and sound promising.
Last edited:
Let's roll!
Or, at least, keep an eye out:

iOS 17.3 Beta Adds New Stolen Device Protection Feature to iPhone
The first iOS 17.3 beta rolling out to developers today includes a new "Stolen Device Protection" feature that is designed to add an additional layer of security in the event someone has stolen your iPhone and also obtained the device's passcode.www.macrumors.com
I am on 17.2 and I know my iPhone 14 Pro already requires Face ID from me to view passwords/passkeys in the keychain. However, there are lots of other features which are clearly new and sound promising.
The problem on the current version of iOS is that it falls back to passcodes if FaceID fails.
This didn't age well.This is why you don’t see Apple doing anything about it as there’s nothing to fix; the fix is with the device user themselves.
I hadn't realised. I don't think I've ever experienced that. Thank you.The problem on the current version of iOS is that it falls back to passcodes if FaceID fails. View attachment 2324215
Maybe Apple should give people the option to enter their full AppleID password instead of the passcode when FaceID fails.
There's a much smaller chance of someone shoulder-surfing a big long password in a bar.
👀
There's a much smaller chance of someone shoulder-surfing a big long password in a bar.
👀
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.

