
Twitter in February 2023 announced that text message two-factor authentication (2FA) is set to become a premium feature for Twitter Blue accounts. Here's why the company's logic behind the decision doesn't make any sense from a security perspective, and why you don't need the feature anyway.

Twitter has said that it will soon be removing text message-based 2FA from non-paying accounts and turning it into a feature that will only be available to subscribers of its premium Twitter Blue offering, which costs $8 per month. This means that any users who don't pay for a Blue subscription and rely on Twitter to send them an SMS text message code to complete the login process will have the feature turned off and removed from their accounts by March 20. Their account password will become the only barrier to access.
Aside from purely financial reasons (presumably it costs Twitter to send you a text), making text-based 2FA a paid-for perk is an odd decision on Twitter's part.
Twitter has justified the policy change by saying, rightly, that SMS 2FA can be abused by bad actors. And there have indeed been "SIM swap attacks" where hackers convinced cell providers to assign a victim's phone number to a device they control, and by taking control of a person's phone number, the hacker can impersonate the victim, as well as receive text message codes to their account. But making SMS 2FA available only to Twitter Blue subscribers simply makes them more susceptible to attacks of this nature.
Twitter says that it is "committed to keeping people safe and secure on Twitter," and it's true that SMS 2FA is better than no 2FA at all, but its policy does nothing to encourage users to switch to a more secure form of 2FA – perhaps because doing so means paying Twitter absolutely nothing.
Switching to App-Based 2FA is the Solution
Rather than rely on SMS-based 2FA, Twitter users should be using a mobile authentication app, like Duo, Authy, or Google Authenticator, or the password authenticator built-in to iOS. App-based 2FA is a far more secure alternative, as it never leaves your device and doesn't involve you receiving a code sent to your phone via text message.
To use this method to secure your Twitter account, first ensure that you have your authenticator app of choice installed on your iPhone. Then follow these steps:
- Launch the Twitter app or log in to the Twitter website.
- Go to your account's Settings and privacy, found in the Settings and Support dropdown menu.
- Select Security and account access -> Security.
- Select Two-factor authentication.
- Check the mark next to Authentication app.
- Follow the prompts, entering your account password when requested.
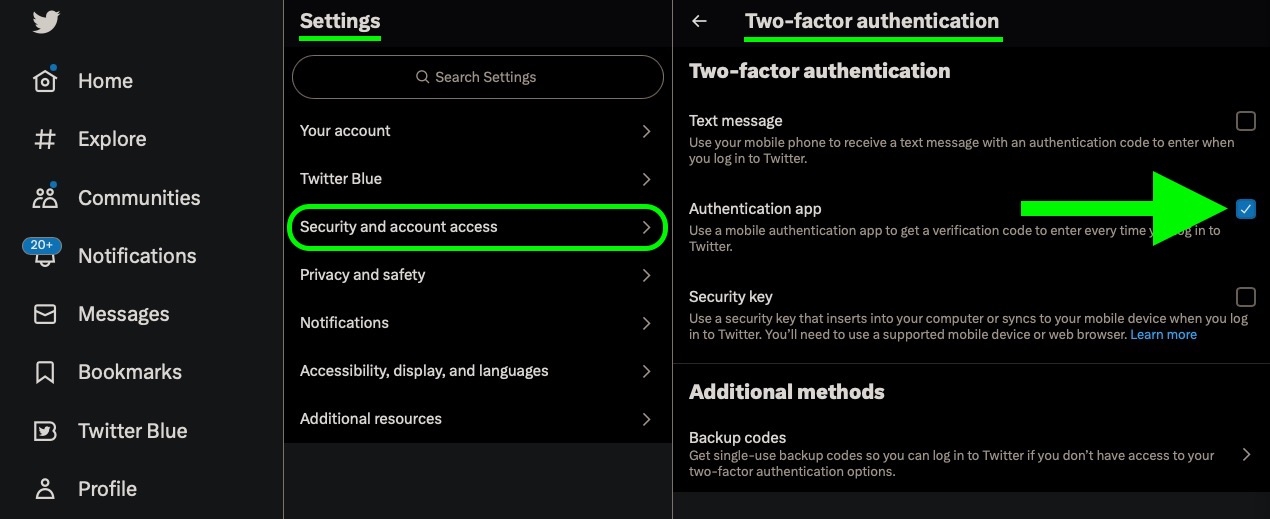
When you've completed the above steps, you should be able to log in to your Twitter account using your password, accompanied by a code generated by your authenticator app. Just be sure to keep a backup of your codes – if you don't have one and you lose your phone, you'll find it a lot harder to access your 2FA accounts.
Article Link: How to Keep Your Twitter Account Secure Without Having to Pay for the Privilege
Last edited:

