
Ahead of the debut of AirTags and support for locating third-party Bluetooth items through Find My in iOS 14.5, a team of security researchers from the Secure Mobile Networking Lab at the Technical University of Darmstadt in Germany has reverse engineered the Find My protocol and developed an app that's designed to let anyone create an "AirTag" based on a Bluetooth-capable device.
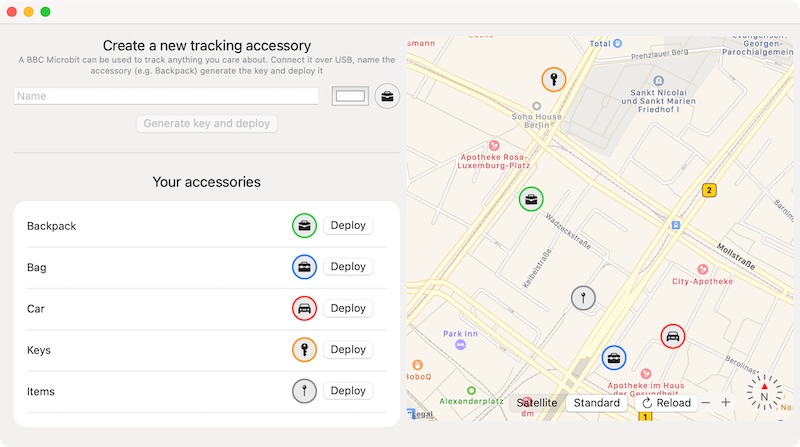
Called OpenHaystack, the app and the source code are available on GitHub for those who are interested in taking a look. The app allows users to create their own Bluetooth tags based on the Find My network by installing an "AirTag" firmware image on a Bluetooth dongle.
The app displays the most recent location of a created Bluetooth tag reported by any iPhone using Apple's Find My network that was implemented in iOS 13, plus it shows the location of the tag on a map.
According to the security researchers, the created tags send out Bluetooth beacons, which are picked up by nearby iPhones that interpret the sending device as lost. The current geolocation is end-to-end encrypted and then uploaded to Apple, with the OpenHaystack app then downloading the encrypted report from Apple and decrypting it locally on the Mac.
In the process of developing this tool, the Secure Mobile Networking Lab researchers also identified a macOS Catalina Find My vulnerability that was reported to Apple and addressed in a 10.15.7 update released back in November. The vulnerability allowed a malicious app to access iCloud decryption keys to download and decrypt location reports submitted by the Find My network.
Apple's iOS 14.5 update includes support for tracking third-party Bluetooth devices in the Find My app using a new "Items" tab, which takes advantage of the same Find My protocol used for the Mac app.
At the current time, in-app tracking is limited to Beats headphones and upcoming Belkin wireless earbuds, but in the future, many third-party Bluetooth devices may include Find My integration, making it easier to keep track of them. This system will also be used by Apple's own rumored AirTags, which have yet to be released.
Article Link: Security Researchers Develop Framework for Tracking Bluetooth Devices Using Find My


