
Apple WebKit engineers have put forward a proposal to make one-time passcode SMS messages more secure by developing a standardized format for the two-step verification process, reports ZDNet.
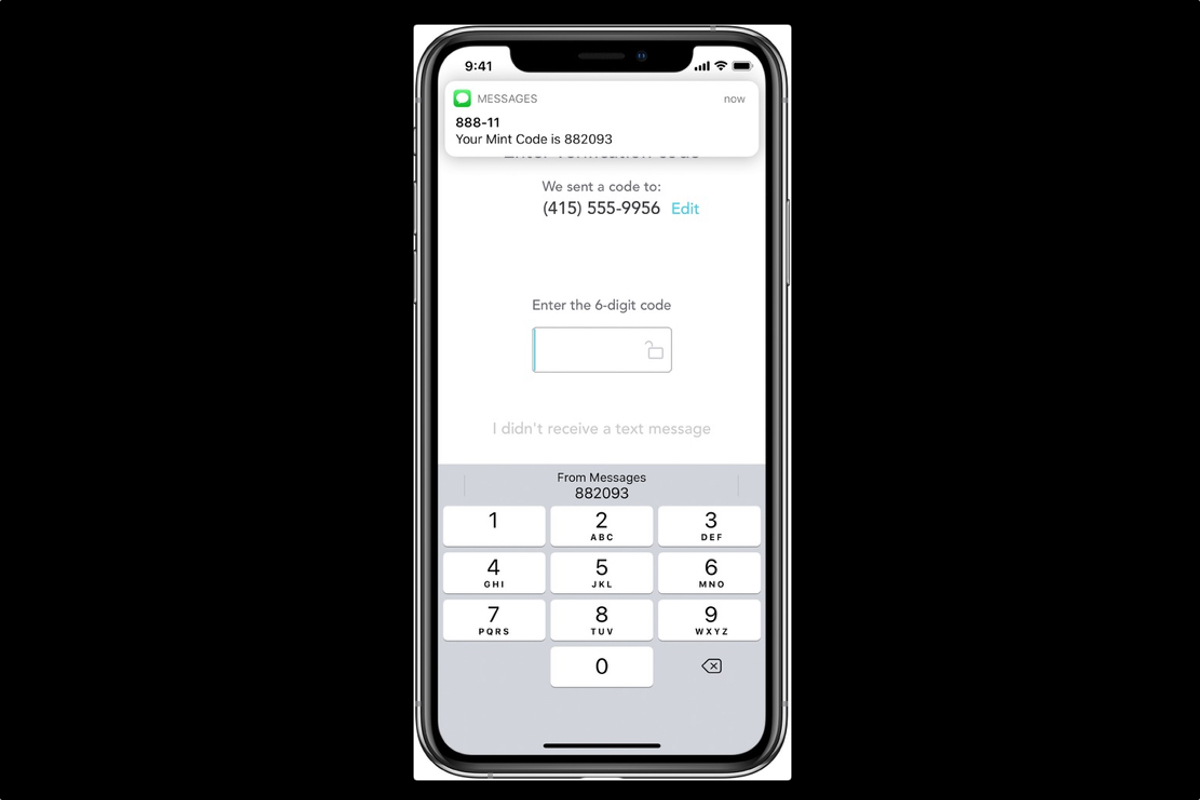
Two-step verification logins require a user's password and another element that only the user would know - in this case, a one-time code sent via text message - to gain access to an online account.
As it stands, these SMS messages can arrive in a variety of formats, making it difficult or impossible for apps and websites to detect them and automatically extract their information.
Apple's proposal has two goals. The first is to introduce a way that one-time passcode SMS messages can be associated with the website, by adding the login URL inside the message itself.
The second goal is to standardize the format of the SMS messages, so that browsers and other apps can identify the incoming message, recognize the URL, and then extract the OTP code for automatic insertion into the appropriate login field on the website.
The idea behind automating OTP entry is that it eliminates the risk of users falling for a scam and entering an OTP code on a phishing site with a different URL.
Apple developers provided the following example of the new format SMS message for OTP codes:
The first line is intended for the user, enabling them to determine the website that the SMS OTP code came from, while the second line is processed by browsers and apps so that they can automatically extract the OTP code and complete the 2FA login operation.747723 is your WEBSITE authentication code.
@website.com #747723
If auto-complete fails, users will be able to check the URL of the website that sent the text against the site they're trying to log in to.
According to the report, Google Chrome engineers are already on board with Apple's proposal, but Mozilla's Firefox team have yet to provide official feedback on the standard.
The new proposals would add another layer of security to Apple's existing security code autofill feature, introduced in iOS 12, that can detect one-time passcodes in Messages and display them conveniently above the user's keyboard.
Article Link: Apple Engineers Propose Standardized Format for SMS One-Time Passcodes
Last edited:

