
Apple in macOS 10.15.3 quietly addressed a bug that left some of the text of encrypted emails unencrypted, reports The Verge.
This particular vulnerability was publicized back in November, after IT specialist Bob Gendler found that the snippets.db database file used by a Siri feature to offer up contact suggestions stored encrypted emails in an unencrypted format.
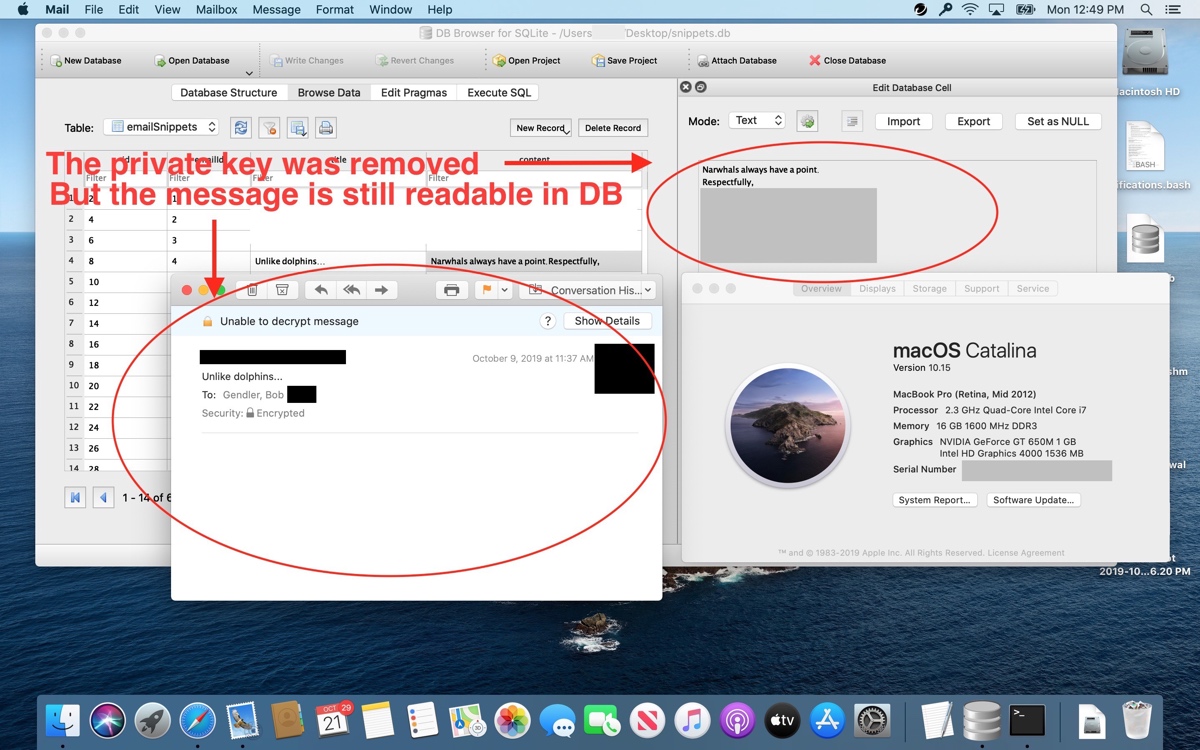
A demonstration from Gendler showing the bug. The image features a private key that has been made unavailable in Mail, rendering the message unreadable. It continues to be available in the database, though.
Gendler reported the bug to Apple in July, but shared details in November after Apple failed to fix it. After the bug was announced to the public, Apple promised that a fix was coming in a future version of macOS.
Only a small number of people were affected by the bug because it required a very specific set of steps to reproduce. It required customers to be using macOS and the Apple Mail app to send encrypted emails. It did not impact those who had FileVault turned on, and a person who wanted to access the information would have also needed to know where in Apple's system files to look and have had physical access to a machine.
Apple didn't mention the bug fix when macOS Catalina 10.15.3 was released last week, but the update does indeed appear address the issue, Gendler told The Verge.
According to Gendler, macOS Catalina 10.15.3 prevents encrypted emails from appearing in Spotlight searches, and the database file that used to include encrypted emails no longer does so.
Article Link: Apple Fixed macOS Mail Vulnerability That Exposed Text of Encrypted Emails in macOS Catalina 10.15.3


