All of this is common sense. You can't expect a 4-digit passcode to be all that secure. If you feel paranoid, use an alphanumeric passcode, aka password, instead.
I use a 29-digit numeric passcode. Easy for me, less easy for shoulder surfers.
All of this is common sense. You can't expect a 4-digit passcode to be all that secure. If you feel paranoid, use an alphanumeric passcode, aka password, instead.
Could be. We’ll see shortly.CASE CLOSED ?

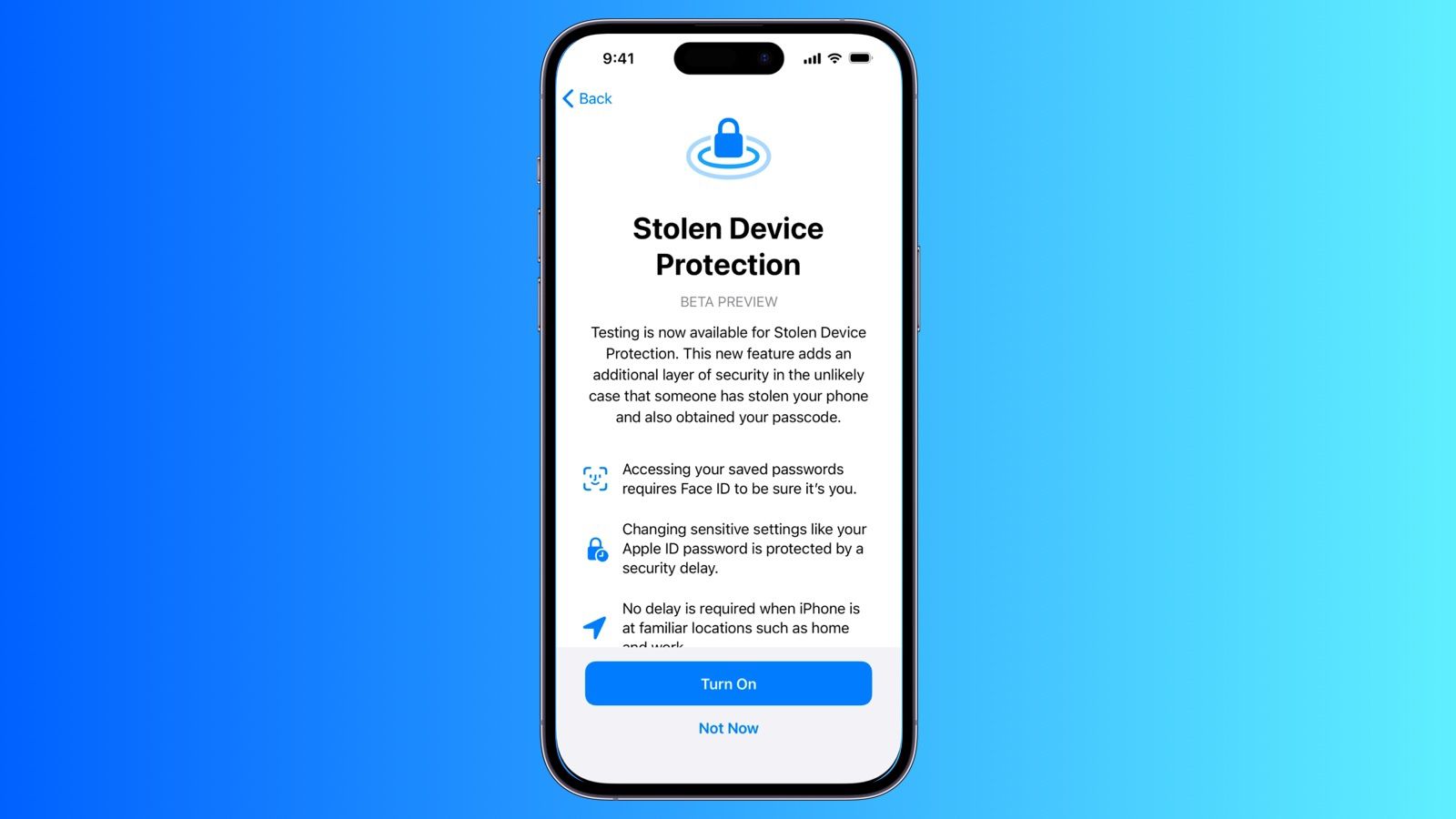
iOS 17.3 Beta Adds New Stolen Device Protection Feature to iPhone
The first iOS 17.3 beta rolling out to developers today includes a new "Stolen Device Protection" feature that is designed to add an additional layer of security in the event someone has stolen your iPhone and also obtained the device's passcode.www.macrumors.com
The description of the Stolen Device Protection feature seems to imply that the user must have Significant Locations enabled (Settings | Privacy & Security | Location Services | System Services | Significant Locations). Otherwise, how will Apple know that an "iPhone is in familiar locations, such as at home or work"?
There are reasons (use cases). Example: I have lots of files in iCloud Drive enabled only in macBook, but disabled in iOS for security reasons (lots of private, sensitive information). SDP doesn't stop thief to enable iCloud Drive in iOS settings if not disabled by ScreenTime options.I don’t see a reason to use Screentime passwords at all with Stolen Device Protection as it stops the entire mechanism thieves were using to change the Apple ID password.
The only way thieves could change the Apple ID password would be to also kidnap the phone owner so that they could use Face or Touch ID to change the Apple ID password even with the 1 hour delay.
There is a slight danger to enabling the stolen device protection, in that if TouchID or FaceID doesn’t work, you are effectively locked out of doing a lot of security related things on the device. I know my Dad’s TouchID doesn’t work in wintertime for some reason. That’s less of an issue with FaceID, but if the person gets into an accident or something the phone could become unusable.
Presumably stole device protection is enabled on a per-device basis so it would still be able to do some account related things on another device.
There are reasons (use cases). Example: I have lots of files in iCloud Drive enabled only in macBook, but disabled in iOS for security reasons (lots of private, sensitive information). SDP doesn't stop thief to enable iCloud Drive in iOS settings if not disabled by ScreenTime options.
My opinion - whole Settings app should be protected by Face/Touch ID when SDP active. For now it is more complicated that it should be.
Disabling access to my files is non-security related topic? That's quite bold statement, really.Stolen device protection (SDF) doesn’t do anything for non-security related features. As neither iCloud Drive nor ScreenTime are considered security, it won’t do anything for that.
For iCloud Drive I would suggest either using password protected files or putting sensitive information in Notes which can be password protected.
The plus side of is that because a thief can’t change the Apple ID password you can mark the device as lost which will disable using the passcode to unlock the phone so the thief will only have a limited amount of time to use the device.
Disabling access to my files is non-security related topic? That's quite bold statement, really.
You're trying to explain Apple's aproach hidden behind the name of the feature. I understand that approach but for me it is bad approach.What I said is iCloud Drive is not a security feature which can result in the device or Apple account being stolen. As such device protection is not designed to prevent access to iCloud Drive.
Stolen device protection (SDF) doesn’t do anything for non-security related features. As neither iCloud Drive nor ScreenTime are considered security, it won’t do anything for that.
But, if Stolen Device Protection (SDP) closes the existing loophole that allows a Screen Time passcode to be reset by changing an Apple ID password, then SDP has substantially increased the robustness of Screen Time itself - correct?
There is a new and interesting video from the Wall Street Journal, in which a convicted thief describes the techniques used to steal an iPhone and its passcode - and, then leverage the valuable contents stored on the device.

