My Apple Watch SE running the latest public WatchOS beta is listed as not having the latest OS version for the upgrade.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Expanded iCloud Encryption Can't Be Enabled From New Apple Devices Right Away
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It depends. Most HSMs do not allow extraction of the keys (that's the whole point). Some allow transfer of wrapped keys for backup or scaling purposes.You’re misunderstanding what Apole is describing here.
Apple is saying they store the keys inside “Hardware Security Modules” which is an Apple specific way of describing a key vault. Apple generates these keys and stores them in this vault which is industry best practice (meaning if you stole a server from the Apple Data Center you won’t be able to decrypt that data since you wouldn’t have the key) on key management and storage. That doesn’t mean that Apple doesn’t have access to this key. They do have access to it.
I can’t wait to turn this on!
It’s not just a “New device.” It’s a new device FOR YOUR APPLE ID - so one you recently signed into (-‸ლ)The last bullet is where the logic breaks down.
Someone can compromise your account and sign in on an old device. Why would someone need to purchase a new device to compromise an account?
I would guess that the new device rule has nothing to do with new devices, but rather to artificially stagger the process of encrypting devices and accounts to reduce the load on iCloud services.
'New device' isn't clearly defined, so a device purchased one year ago can be considered 'new' for all intents and purposes.
Sorry for dumb question, but what's FUD stands for?The FUD is strong in this thread.
- If you have a device that’s been active for a while, you can turn it on.
- If you turn it on, it’s on for ALL devices.
- The reason you can’t use a recently activated device, is so if someone compromises your account and signs in on a device, they can’t lock you out of your data.
Fear, Uncertainty, Doubt. It's a flavor of misinformation meant to maintain the status quo often identified in tech circles, especially related to nebulous or yet-unproven tech. see also IBM in the 70's, MS in the 90's.Sorry for dumb question, but what's FUD stands for?
Fear Uncertainty and Doubt.Sorry for dumb question, but what's FUD stands for?
Obviously, a keystore can vary in its implementation. The E2EE method Apole implements uses a hardware key manager that is on the device and doesn’t allow pulling the key off the device. You can read all about that in their T2 and similar white papers on how the handle encryption keys for data that Apple doesn’t get the key to.It depends. Most HSMs do not allow extraction of the keys (that's the whole point). Some allow transfer of wrapped keys for backup or scaling purposes.
But, as I said earlier, Apple needs to be able to read the key prior to the changes being discussed here. As how else would iCloud.com work? You can access it without your iPhone and Apple isn’t storing your password on their servers to decrypt data either.
Also, Apple encryption keys that use the user’s codes as a portion of the key to ensure it is unknown to Apple use the device passcode not the Apple account password. This is why you can be asked to enter the passcode for a previous device when migrating to a new one. You’ll never be asked for such as password signing into iCloud.com.
Thanks😊Fear, Uncertainty, Doubt. It's a flavor of misinformation meant to maintain the status quo often identified in tech circles, especially related to nebulous or yet-unproven tech. see also IBM in the 70's, MS in the 90's.
Is there any information regarding support for older OSes? Would enabling this feature block some old versions from accessing most iCloud features? Or is this just that the coming update that adds the ability to transition your account to this? Considering when one logs in on an untrusted machine, there are trust factors in place requiring a second trusted device to add the device to the fold, which presumably exchanges private keys which, with this enabled, would become fully private instead of unencrypted or unlockable on the server by other parties. And, as LogicalApex mentioned, the T2 and other security chips hold tightly on to any hard keys. Tho combining these points in a similar vein makes me wonder how the browser instance of iCloud works in this, in that a 3rd-party untrusted machine's browser (just software) could still access it, with some cooperation of a trusted device... so it is still more than just a password, but I'm not a security person, so it's hard for me to wrap my head around the exchange. (waves hands) WebAssembly.. I dunno.
The way the article is worded -- "new device" rather than something like "device newly associated with a certain Apple ID" -- plus the Twitter posters that missed the point of why this delay has a security purpose, contributed to a lot of confusion.It doesn't matter if the device is new or old. What matters is how long the device that wants to enable advanced protection has been registered to the Apple ID.
When reading the article my first thought was that it meant "new device" -- either newly purchased or newly manufactured or newly released, which would not make sense.
The fact is that it applies to any device newly associated with that Apple ID, so that a hacker who has the credentials cannot log in to a victim's account and then lock out the victim, with the victim having no way to recover the data.
There's a list of trusted devices in your iCloud account. You probably can only enable the feature if the device is currently and has been on that list for long enough, uninterrupted. If you were to sell a device you no longer want, standard procedure is to log out of icloud on there, and remove it from the trusted devices list on iCloud (I forget if this is automatic). Even if someone were able to acquire your old device and log in as you and re-add it to the trust list, it's still a "new"ly added device now. Or so I presume.
based on somebody else's screenshot on this thread you are unable to activate advanced data protection if any of your devices are before a certain version. I suspect you wouldn't even be able to login to an iCloud account with ADP enabled using an older version.Is there any information regarding support for older OSes?
While inconvenient this makes sense to me. The older device would be forced to interact with iCloud in the traditional way and would have the same constraints that regular data protection offer today.
I just added my 14 on launch day but didn’t have a waiting period. It told me I had to update everything to the RCs. I updated everything to RCs and there were no waiting period. I wonder why?
Thanks for pointing this out. Good find.based on somebody else's screenshot on this thread you are unable to activate advanced data protection if any of your devices are before a certain version. I suspect you wouldn't even be able to login to an iCloud account with ADP enabled using an older version.
While inconvenient this makes sense to me. The older device would be forced to interact with iCloud in the traditional way and would have the same constraints that regular data protection offer today.
From the screenshot, it does look like it *requires* the "latest" OS. So not as simple as an existing key exchange that upgrades to lock out other parties, but a new mechanism requiring an OS update... Honestly, it doesn't pass my sniff test tho, feeling like a very hard edge of obsolescence and why it's optional. If this is the case, any recently unsupported (even if its getting security updates) could be omitted. Maybe even Monterey and iOS15. I do have even older unsupported OSes that technically still can log in, but lack all the features (either by lacking an OS app, or incompatibly old). This link has a good list of what works with what past OS still, but enabling the new security hard breaks it. https://support.apple.com/en-us/HT204230
I want to enable it, but I'll wait a bit. Cheers!
Imagine how many people will forget their encryption key and lose data on this.
Not sure on the reasoning behind keeping experienced users from being able to activate this feature.
Very excited about this coming to Canada.
That's why this is deliberately OPT-IN. When turning this on, the user is assumed to understand the risks and will have been asked to either give a second user permission to help unlock or to print and store the key somewhere. You'd need to have deliberately opted into this, AND forgotten your Apple ID login, AND lost the key or lost contact with the second person who's able to help you unlock. This isn't your typical grandma lapse.
The FUD is strong in this thread.
- If you have a device that’s been active for a while, you can turn it on.
- If you turn it on, it’s on for ALL devices.
- The reason you can’t use a recently activated device, is so if someone compromises your account and signs in on a device, they can’t lock you out of your data.
I would also think, but we shall see, that enabling ADP will be an option when you first set up a new iCloud account.
The safeguards against malicious actors locking you out of your own account sound entirely sensible, but every new account will by definition have a newly associated device and it would make absolutely no sense to have a mandatory waiting period before you can turn on the feature on your brand new account with a single device associated with it.
FreakinEurekan forgot to add an additional bullet point:This needs to be the top post.
• The Sky is not falling
Should be an option to enable from new device immediately. Maybe in the future, Apple will provide one.
I just created a YouTube channel under a new gmail account and put all my photos and video on there where I know no one will view it.
Reverse card 😂
I think I have like 13 subscribers for posting nothing
Imagine how many people will forget their encryption key and lose data on this.
Not sure on the reasoning behind keeping experienced users from being able to activate this feature.
Very excited about this coming to Canada.
Because it can be used to lock the user out in an attack.
Say, I hack your iCloud, register my iPad with your account, and enable E2E. Now, Apple no longer has your encryption key and you don't either. Only I have your key. You are permanently locked out. There is no way you can regain access to your account after an attack like this. The waiting period gives you a buffer to prevent this kinda thing. You can still enable this on an old device, and it will take effect immediately on your new device too.
Last edited:
Starting with iOS 16.2, iPadOS 16.2, and macOS 13.1, all of which are expected to be released next week, users have the option to enable a new Advanced Data Protection feature that expands end-to-end encryption to many additional areas of iCloud, including Messages backups, Photos, Notes, Reminders, Voice Memos, and more.
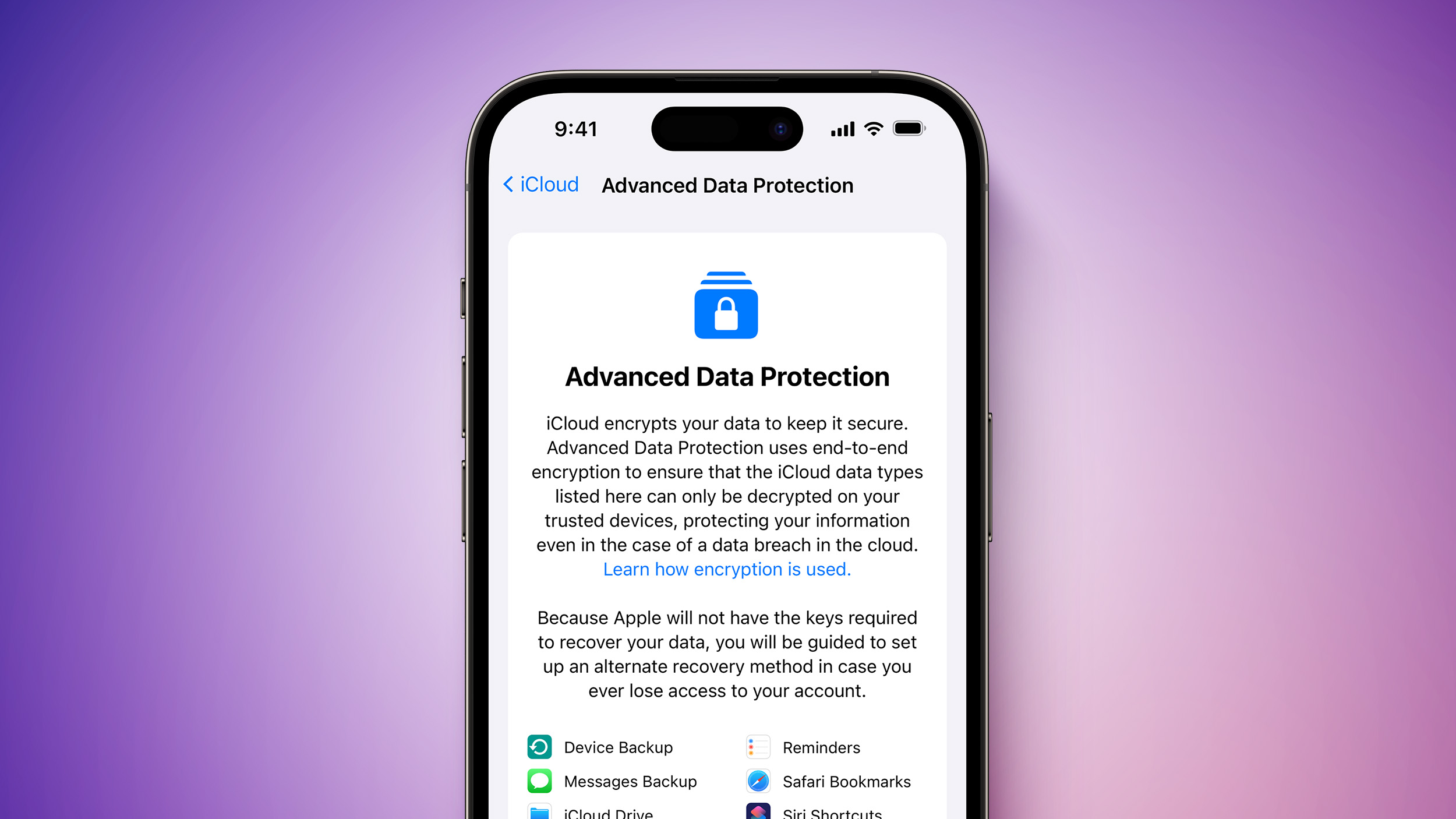
To protect users, Apple does not allow Advanced Data Protection to be enabled from a brand new device for an unspecified period after the device was first set up and added to a user's Apple ID account. We have seen dates range from late January to early February for when users will be able to turn on the feature from a new device. This buffer helps to prevent a malicious actor from enabling the feature if a user is hacked.
Users can still enable Advanced Data Protection from an older device they added to the same Apple ID account, such as another iPhone, iPad, or Mac. In this case, all devices added to that Apple ID account are fully protected by the expanded end-to-end encryption for iCloud, including newer ones that are still in the waiting period.
Turning on Advanced Data Protection removes your encryption keys from Apple's servers for the iCloud categories protected by the feature, ensuring that your data remains secure even in the case of a data breach in the cloud. When the feature is enabled, the encryption keys are only stored on your trusted Apple devices, meaning that they cannot be accessed by Apple or others. The feature can be turned off at any time, at which point your devices will securely upload the encryption keys to Apple's servers again.
When Advanced Data Protection is enabled, access to your data via iCloud.com is disabled by default. Users can turn on data access on iCloud.com, which allows the web browser and Apple to have temporary access to data-specific encryption keys.
iCloud already protects 14 data categories using end-to-end encryption by default, without Advanced Data Protection enabled, including passwords stored in iCloud Keychain, Health data, Apple Maps search history, Apple Card transactions, and more. Apple has a support document with a chart detailing what is protected by standard levels of encryption and what is protected by Advanced Data Protection when enabled.
Advanced Data Protection is available for U.S. users only at launch and will start rolling out to the rest of the world in early 2023, according to Apple. For more details about the feature, read our coverage of Apple's announcement earlier this week.
Article Link: Expanded iCloud Encryption Can't Be Enabled From New Apple Devices Right Away
The reasoning does not make sense. If an attacker got hold of the user’s account, what prevents that attacker from:
- Changing the iCloud Password
- Removing existing iCloud Devices
- Locking the user out of his account
- Making copies of or and/or deleting or modifying a user’s existing data, effectively preventing the user from accessing their data while they still have access to it.
So whether or not advanced data protection can be enabled with a new device or not, does little good to the user.
I recognized that with advanced data protection, a lot of users who don’t know what they’re doing will lose access to their data without an attacker at all (i.e. losing the recovery key or rotating it and only holding on to the old one without realizing that it rotated).
Today, with all my “old apple devices” and knowing that no one has hacked me, I should have an opt-in option that states:
“When I get a new Apple Device, allow Advanced Data Protection to be enabled on that new device after [Textbox: 0-100] days. I recognize that if it’s an attacker’s new device both me and apple will lose access to the data forever”.
And let the user make the choice and take the risk.
Also, Apple has not clarified whether or not turning off or on Advanced Data Protection causes the public/private key to rotate, or if the “old key” they supposedly “promise to delete” still works, even after advanced data protection is on, if say, “a bug” prevented the key deletion to happen from iCloud or, say, data replication causes that key to continue to exist “somewhere in a server” for a period of time even after Advanced Data Protection is on.
Feels like there are too many loopholes, and Apple is “unwilling to fully let go” from user’s private data.
So Apple’s reasoning is that by restricting turning on/off Advanced Data Protection (iCloud encryption) to “old” devices, prevents you being locked out of your data without your permission.
The fallacy is that there’s many more ways someone can lock you out of your data without your permission. For example, someone who gains access to your account can change your password, delete your files, encrypt your files, remove your devices, etc.
So either Apple is stupid, or the real reason for this policy is something else. This policy conveniently gives Apple and third parties (governments) an opportunity to make a copy of a new Apple user’s unencrypted data before they are able to turn on the encryption, thereby rendering the encryption of existing data useless. It’s like giving someone the keys to your safe, they can peek and take pictures, then changing the lock, falsely assuming they don’t know what’s inside your safe.
The fallacy is that there’s many more ways someone can lock you out of your data without your permission. For example, someone who gains access to your account can change your password, delete your files, encrypt your files, remove your devices, etc.
So either Apple is stupid, or the real reason for this policy is something else. This policy conveniently gives Apple and third parties (governments) an opportunity to make a copy of a new Apple user’s unencrypted data before they are able to turn on the encryption, thereby rendering the encryption of existing data useless. It’s like giving someone the keys to your safe, they can peek and take pictures, then changing the lock, falsely assuming they don’t know what’s inside your safe.
And someone has a device, has your Apple login info, then what? You will lose everything.Should be an option to enable from new device immediately. Maybe in the future, Apple will provide one.
As long as you have an existing device on you account already, why does it matter?
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.


