
An exploit allows messages and additional data to be sent across Apple's Find My network, according to the findings of a security researcher.
Security researcher Fabian Bräunlein has found a way to leverage Apple's Find My network to function as a generic data transfer mechanism, allowing non-internet-connected devices to upload arbitrary data by using nearby Apple devices to upload the data for them.
The Find My network uses the entire base of active iOS devices to act as nodes to transfer location data. Bräunlein explained in an extensive blog post that it is possible to emulate the way in which an AirTag connects to the Find My network and broadcasts its location. The AirTag sends its location via an encrypted broadcast, so when this data is replaced with a message, it is concealed by the broadcast's encryption.
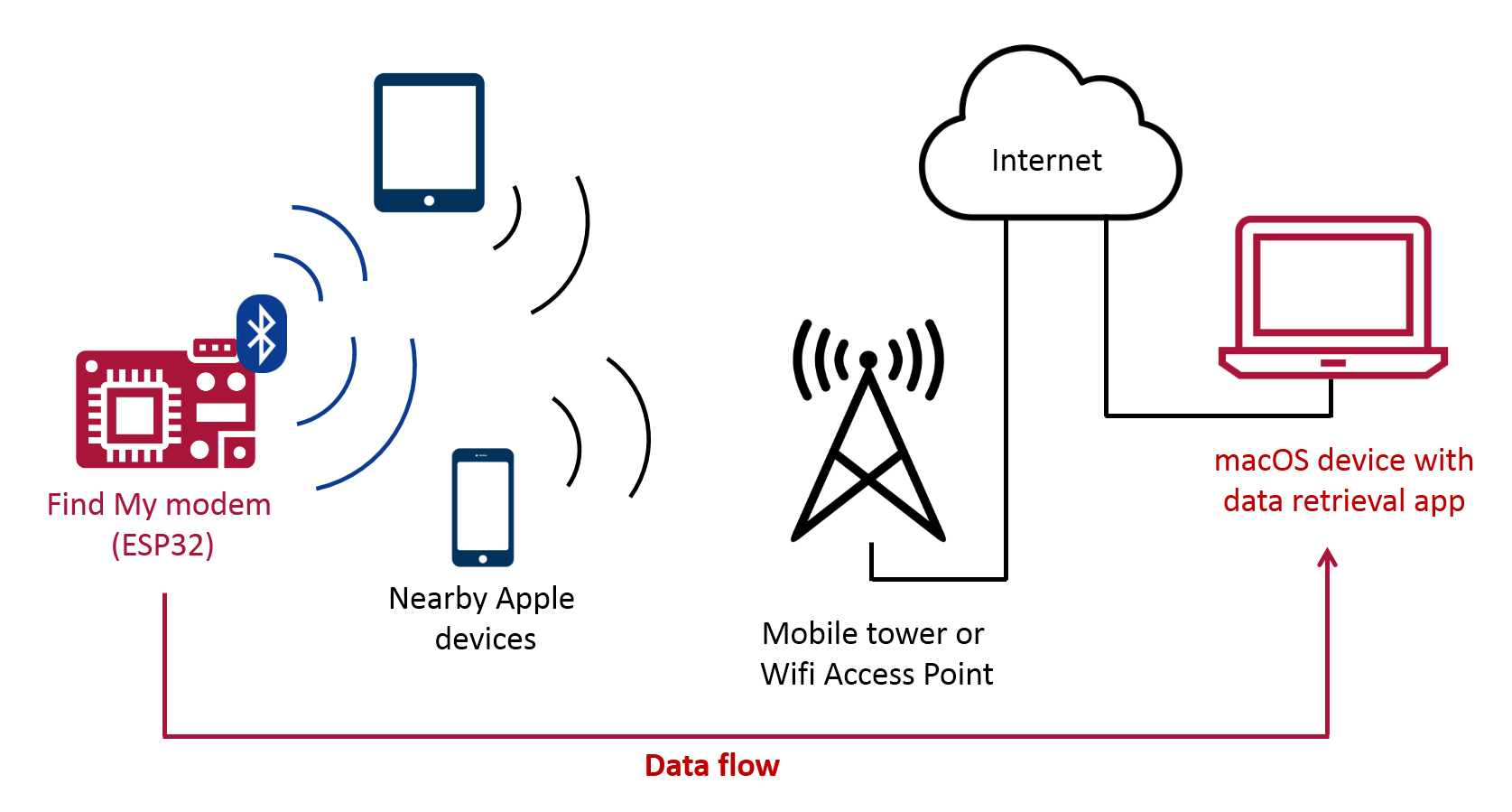
Bräunlein's practical demonstration showed how short strings of text could be sent from a microcontroller running custom firmware over the Find My network. The text was received via a custom Mac app to decode and display the uploaded data.
It is not immediately clear if this Find My network exploit could be used maliciously or what useful purposes it may serve. Nonetheless, it seems that it could be difficult for Apple to prevent this unintended use due to the privacy-focused and end-to-end encrypted nature of the system.
For more information, see Bräunlein's full blog post, which explains in detail the entire technical process behind passing arbitrary data through the Find My network.
Article Link: Find My Network Exploited to Send Messages

