There's not Manage Plug-ins option on Apple Mail on my Mac. M1 running Big Sur 11.3.1. Perhaps it's disabled on Apple Silicon. Who has, or doesn't have it?Weird because am running it in Big Sur with zero problems.
You can manage plug-ins via preferences -> General -> Manage Plug-inns (at the very bottom of the dialog box).
The plug in is highly non intrusive, it has a "dot" with an X in it if there is nothing to block, and shows up blue if there is.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
How to Prevent Emails From Tracking You in Apple Mail
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
There's not Manage Plug-ins option on Apple Mail on my Mac. M1 running Big Sur 11.3.1. Perhaps it's disabled on Apple Silicon. Who has, or doesn't have it?
I have the "Manage Plug-ins ..."button in Mail. macOS 11.3.1. 2018 Mac Mini.
And there is a downloadable installer for MailTrackerBlocker: https://apparition47.github.io/MailTrackerBlocker/
Are you using the iCloud for Windows control panels? https://support.apple.com/en-us/HT204283I'm not a big fan of Apple Mail either, but Outlook is seems more cumbersome when it comes to dealing with iCloud accounts. And in order to view iCloud calendar appointments in Outlook, you have to first to publish each calendar in iCloud (make it public) in order for Outlook to be able to import it.
But I understand the attraction to Outlook. I would love it if Apple would come out with an all-in-one that had mail, calendar, and contacts all in one app.
Have you tried Thunderbird? TBSync does a great job of keeping my iCloud, Google, and Yahoo accounts all synced.
Precisely. I think the MacRumors author this time didn't do their homework...Not to be overly pedantic, but there is no “code within the pixel” as is stated in the article. Rather, the mail client sees the image file (which can be as small as a single pixel) and triggers and download of the image asset from the server; it is the downloading of this image by the client that provides the data as to whether (and potentially where) the email was accessed.
Oh no please don't. I really hate that when I had to use PC.I would love it if Apple would come out with an all-in-one that had mail, calendar, and contacts all in one app.
Strange, it's there on my M1 MBA.There's not Manage Plug-ins option on Apple Mail on my Mac. M1 running Big Sur 11.3.1. Perhaps it's disabled on Apple Silicon. Who has, or doesn't have it?
Attachments
Solutions like this are great, but after a year or two they typically stop working for one reason or another; often because of how Apple handles add-ons. And if you're managing a couple of computers for yourself, a couple for your family and equal number of phones!And how often does this application's blocklist get updated?
And will this help if you read the mail on your phone first?
I've never seen a spam email with Gmail.The vast majority of users out there tearing their hair out over the 10:1 spam vs real emails they get would have no idea how to do this. There needs to be a vastly better and easier way to do this (including jail sentences, huge fines, public floggings, sterilization, or any/all of the usual Medieval tortures for spammers). I would gladly live in a world where each email or text I sent cost me a small fee if it meant spammers couldn't afford to do what they do.
There's not Manage Plug-ins option on Apple Mail on my Mac. M1 running Big Sur 11.3.1. Perhaps it's disabled on Apple Silicon. Who has, or doesn't have it?
Attachments
You expect average people and layman users to dig into the source code to check for malicious/compromising code?Goodness, it's open-source. The beautiful thing about that is that if you don’t trust it outright, dig in and look at the source yourself to see when and where it makes uploads. It does what it says on the tin and doesn’t phone home.
The best security is often the simplest. And in this case people should be aware this open-source plugin however useful, was created by one guy, who manages it and updates it at will, and by installing it you trust him and his open source plug-in to monitor all of your emails for the content which it then filters for you.
You play it off like it’s no big deal, that being open source is good enough reason to hand over permissions, and that is why people end up on the receiving end of scams or worse. It is a big deal for a person to hand over the ability to monitor all their emails to some little known 3rd party plug-in, and people should be hesitant to take that lightly.
Having the source code available publicly is an inherent incentive against trying to do anything hinky because the risk of such activity being exposed is so high, but even then, one wouldn’t have to look at the code. This project has been downloaded more than 2,800 times, including by those with the technical knowledge to know when something fishy is afoot, whether that’s through examining the source code or tools like Little Snitch which would reveal suspect network requests coming from the Mail app. Hell, you could probably look for excessive packets sent using just macOS’s included Activity Monitor app.You expect average people and layman users to dig into the source code to check for malicious/compromising code?
The best security is often the simplest. And in this case people should be aware this open-source plugin however useful, was created by one guy, who manages it and updates it at will, and by installing it you trust him and his open source plug-in to monitor all of your emails for the content which it then filters for you.
You play it off like it’s no big deal, that being open source is good enough reason to hand over permissions, and that is why people end up on the receiving end of scams or worse. It is a big deal for a person to hand over the ability to monitor all their emails to some little known 3rd party plug-in, and people should be hesitant to take that lightly.
I can tell you that it certainly wouldn’t make sense for any network requests to come from Mail via MailTrackerBlocker because, for better or worse, its tracker blocking rules are hardcoded into the software. Rather than self-updating its block list from a source on the Internet, to update the rules you must update the software itself. If you do not wish to install an update, you are not at any point required to do so. You’re also free to remove the software at any time should you wish to and instead go with the garbage “solution” that is disabling all remote images.
Besides, if you think several people who’ve implemented this feature in their free time (because Apple, the self-styled One True Protector of Privacy, has failed to do so) have the capacity and/or desire to set up the requisite servers to surreptitiously receive and analyze likely tens of thousands of email messages per day, via publicly available code, for God knows why, that’s certainly your prerogative. But I’ve certainly heard more reasonable conspiracy theories.
Mind sharing how you're achieving this? I've been looking for a simple solution for this for a while.I used a unique email address for each service I sign up for that way if I start getting spam I can block that email address.
There’s an even better way for macOS that blocks trackers while still allowing you to view images.
Not a very good solution since it relies on a static blacklist. there should be some auto-update mechanism instead of manually update the list every time.
I'd say the best solution is to let Mail.app HTML render engine use Safari content-blocker extensions.
lol thanks for that *better* description. The way this article was written made me chuckle.WTF? Tracking images are creepy, but let's not pretend they're magical, because they're not. You get an email. It's full of HTML, because nobody does plain text email any more (sigh). Because it's HTML, it can specify images to load. One of them is an image on the sender's server (eh, probably all of them are images on the sender's server - that's how the web works). The act of requesting that image from the remote server leaves a log entry in the remote server (which is how the web has always worked). If they gave the pixel image a name that's unique to you (not your name, just a random number they've associated with you), then they can infer, because that image was requested from the server, that you requested it (by opening the email), and they know when, because the server logs when it fulfills requests, and by looking the requesting IP address up in a geolocation database, they can get an approximate location. But you make it sound like the pixel image itself is actively transmitting information - it's not - there's no "code within the pixel", it's just an image.
You must not have set upThis doesn't work. There doesn't seem to be an option in Apple Mail anymore to manage plug-ins.
This doesn't work. There doesn't seem to be an option in Apple Mail anymore to manage plug-ins.
I've been using MailTrackerBlocker which is what was referred to but not by name on 4 Macs successfully for a few months now. I get to see all my loaded images, and the utility shows in each email what it found (if anything). Highly recommended.The aforementioned plug-ins don't seem to be installable as there isn't an option to manage plug-ins in Apple Mail anymore.
I don't want to block images in Apple Mail - so this is already a hassle as it will disable some features in emails I want to keep visible/usable. I am still using Little Snitch to do the heavy lifting in this department, it seems to work fine, and I'm used to the pop-ups.
How is Homebrew support for M1 Macs? Or, perhaps a better question, any ideas on how many Homebrew apps have been updated to native ASi support vs. having to run through Rosetta?There’s an even better way for macOS that blocks trackers while still allowing you to view images.
Blocking automatic image loading is a great way from preventing the email platform/server from tracking the open, however, clicking any link in that email will likely automatically trigger an open and click simultaneously. I would argue most if not all email platforms are tracking open and click at a minimum.
Extra fun fact: Your email address (not best practice) and/or unique identifier is also being used to trigger programmatic ads in newsletters and marketing emails. This data can be shared with third party companies to measure campaign effectiveness.
Extra fun fact: Your email address (not best practice) and/or unique identifier is also being used to trigger programmatic ads in newsletters and marketing emails. This data can be shared with third party companies to measure campaign effectiveness.
Having the source code available publicly is an inherent incentive against trying to do anything hinky because the risk of such activity being exposed is so high, but even then, one wouldn’t have to look at the code. This project has been downloaded more than 2,800 times, including by those with the technical knowledge to know when something fishy is afoot, whether that’s through examining the source code or tools like Little Snitch which would reveal suspect network requests coming from the Mail app. Hell, you could probably look for excessive packets sent using just macOS’s included Activity Monitor app.
I can tell you that it certainly wouldn’t make sense for any network requests to come from Mail via MailTrackerBlocker because, for better or worse, its tracker blocking rules are hardcoded into the software. Rather than self-updating its block list from a source on the Internet, to update the rules you must update the software itself. If you do not wish to install an update, you are not at any point required to do so. You’re also free to remove the software at any time should you wish to and instead go with the garbage “solution” that is disabling all remote images.
Besides, if you think several people who’ve implemented this feature in their free time (because Apple, the self-styled One True Protector of Privacy, has failed to do so) have the capacity and/or desire to set up the requisite servers to surreptitiously receive and analyze likely tens of thousands of email messages per day, via publicly available code, for God knows why, that’s certainly your prerogative. But I’ve certainly heard more reasonable conspiracy theories.
I like the idea of the plug-in and I hope Apple implements a feature like this into the native Mail app. And you may be right that this Plug-in is trustworthy in it’s reputation and operations. However I would advise caution when giving away broad permissions over your big communication apps. If you’re unsure, don’t install.
I'll pass along how –I– do this. My hosting provider, Pair.com, uses qmail as a mail server, and qmail supports Sub-Address Aliasing through its qfiltering mechanism. So I can create a "recipe" of the form "'account'-default@mydomain.tld" that accepts mail addressed to the "account" dash "anything" address. I can then filter locally on the "anything". I create a bunch of rules for TLDs, like "com-default", "org-default", "info-default", etc, and have them dumping the inbound mail into an IMAP folder of my account, while blocking the com@/org@/info@ main account addresses.Mind sharing how you're achieving this? I've been looking for a simple solution for this for a while.
For example: a 'com-default' rule would catch com-amazon@mydomain.com, and I can give that address to Amazon, using their top-level domain, without me having to make a specific Amazon rule. If/when Amazon loses their email database to spammers (better example might be Zappos, or Dropbox, or Adobe, all who lost their email databases), I can first put heavier anti-spam rules on JUST "com-amazon@mydomain.com", again using the qmail rules mechanism. Could say, for instance, that if the sender for that specific address isn't "from @amazon.com", then trash it. Or, if the spam gets too bad, I can just block that specific address entirely, without effecting other "com-*" addresses! Finally I block all mail to "com@mydomain.com".
This gives me a ton of flexibility. I just use the B2C's domain as a "unique" address AND I get to see who is selling my addresses. Or has had a security breach.
Gmail also supports sub-address aliasing, using the "+" delimiter. However, it is terribly ineffective because Google (stupidly) doesn't let you select an alternate "account" (the front part, before the +) for a gmail address, so any spammer that sees account+something@gmail.com knows that account is a legit Gmail account, can drop the +something, and hit the Inbox directly. You can kinda wrangle around this with creative use of "." in the address, but, again, spammers know that they can just drop "." without consequence. Though it does give you a bit of leverage: if you use, say "f.roo+amazon@gmail.com" and start getting mail at "froo+amazon@gmail" or just "froo@gmail.com", you know it is spam (since you can assume if they're dropping "." and "+*" they're up to no good).
Outlook supports sub-address aliasing too, similarly using "+", but again suffers from the same stupidity as Gmail and doesn't, I don't think, allow "." usage. Also, it doesn't work on 365 Business addresses. Nor can you can't address aliasing with M365 Personal/Family.
However many web forms won't even ALLOW "+" in the account portion of an email address, which technically violates the RFC, since + and - are allowable address characters. I have had better luck with "-". IIRC, Comcast does this. (Comcast won't even let you USE an email address with "comcast" in it.)
I had, long ago, mused upon a much better solution: using an encryption algorithm to generate addresses on-demand. When Apple came out with their Sign in with Apple ID email thing, I had high hopes. Unfortunately, their solution falls short since the entire system hinges on mail redirection within SMTP (which is fraught with danger). The best solution is one that would run on the front end of your mail server, using your domain, and be able to quickly reject blocklisted inbound addresses. Although black-holing them is also a valid solution too. And I want encryption so that addresses can't be easily guessed. Apple really is the only one that can do this effectively, since they have the predominant position at the mail client and the browser. Need the mail client to "unwrap" the address portion for local filtering as well as report back "spam" addresses to the blacklist on the server. Need the browser to be able to generate the unique addresses in webforms and push that data to the server/password list. And finally need an open-sourced algo to generate the addresses which could be deployed to mail servers. The best solution would tie together the encrypted address with SPF records; if a message's decrypted address's domain doesn't yield a SPF record matching the message's sender, that's a pretty good indicator it is spam. But, going back to the SMTP rerouting, that can't be known for sure. And it requires a good bit of computation upfront. (But, IMHO, better than wasting my time with spam.)
No clue how this works on M1 Macs, sorry. Since it’s made for macOS 11, I’d cautiously assume that it works.How is Homebrew support for M1 Macs? Or, perhaps a better question, any ideas on how many Homebrew apps have been updated to native ASi support vs. having to run through Rosetta?
I’ll take articles like this over Memoji news or wristband showcases any day. It would be nice if we could filter a lot of the later articles out for a more Mac|iPhone|privacy (or just less fluff) focused experience.
mail is in desperate need for a complete code delete then rebuild from scratch. No more UI changes vs functionality to modernize it.
You JUST made me realize that this is totally deliberate to coerce people to allow secret tracking. Yikes.I’ll check this out when I have time. I’ve gotten tired of how hard some emails can be to read without all the images.
That’d be a decent solution, but the software does also include a generic rule which blocks many unrecognized trackers by simply blocking any <img> tag with a width and height of 0 or 1 px, regardless of the source.Not a very good solution since it relies on a static blacklist. there should be some auto-update mechanism instead of manually update the list every time.
I'd say the best solution is to let Mail.app HTML render engine use Safari content-blocker extensions.
The button will only show up once you have installed the Plug-in! Just use the installer shown in the link that MevetS has posted above. I have it working on Big Sur too.I have the "Manage Plug-ins ..."button in Mail. macOS 11.3.1. 2018 Mac Mini.
And there is a downloadable installer for MailTrackerBlocker: https://apparition47.github.io/MailTrackerBlocker/
Have used this setting for ....what , decades now? Very 'old school' but still a good tip for those who didn't know. Prevents more than just 'tracking'!
Apple's App Tracking Transparency feature is designed to allow users to opt out of the surreptitious tracking that third-party apps have traditionally relied on for ad targeting purposes. But tracking can go on in your email inbox, too.

Unsolicited marketing emails will sometimes know whether you've opened their email, and if so, when you did so. They can even know where you were at the time, thanks to tracking methods employed by marketing platforms like MailChimp.
The way they track is very discreet and kind of creepy. Embedded in the email will be a tracking pixel, often hidden within a signature image or a link. When the message is opened in your email client, code within the pixel silently sends this information back to the company.
Some email account providers attempt to limit this sort of tracking by routing images through proxy servers, for example, which hides your location. But there's actually a simple way of preventing tracking pixels altogether, and that's by disabling the automatic loading of images in your email client.
The following steps show you how to disable automatic image loading in Apple Mail for macOS, and below them, you'll find instructions to do the same in iOS.
If you're using Mail for iPhone or iPad, you can find the same setting in the Settings app. Tap Mail, look under "Messages," and turn off the toggle next to Load Remote Images.
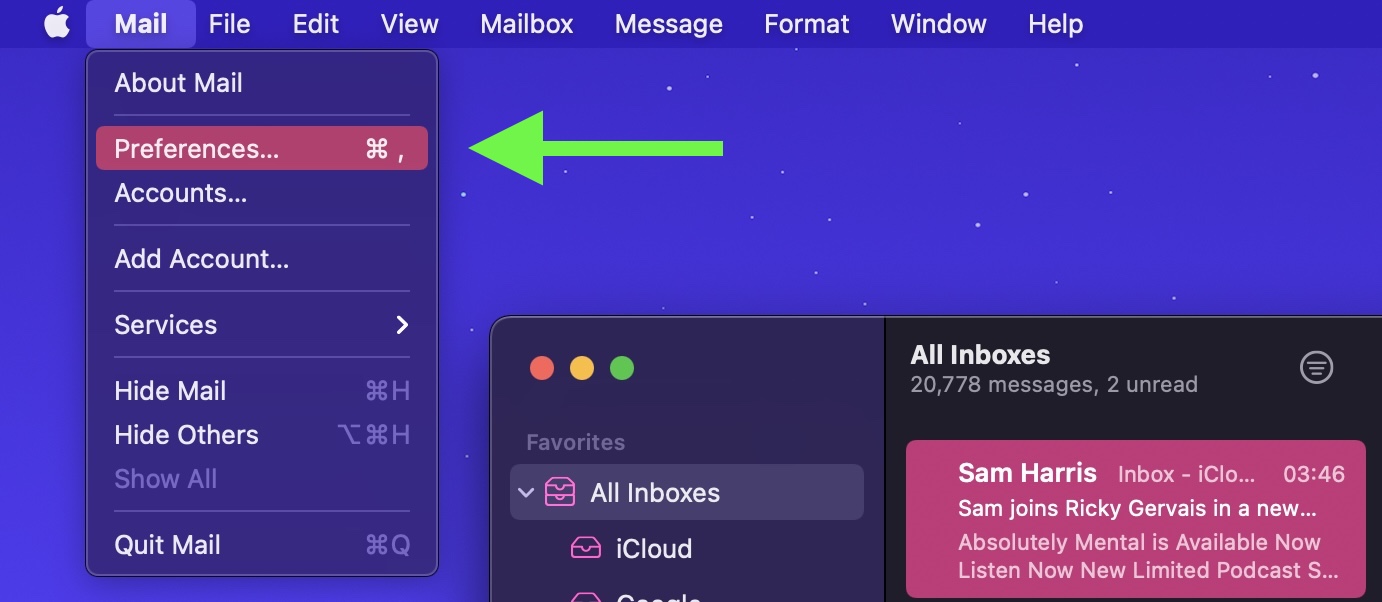
- Launch Apple Mail.
- Select Mail -> Preferences from the menu bar.
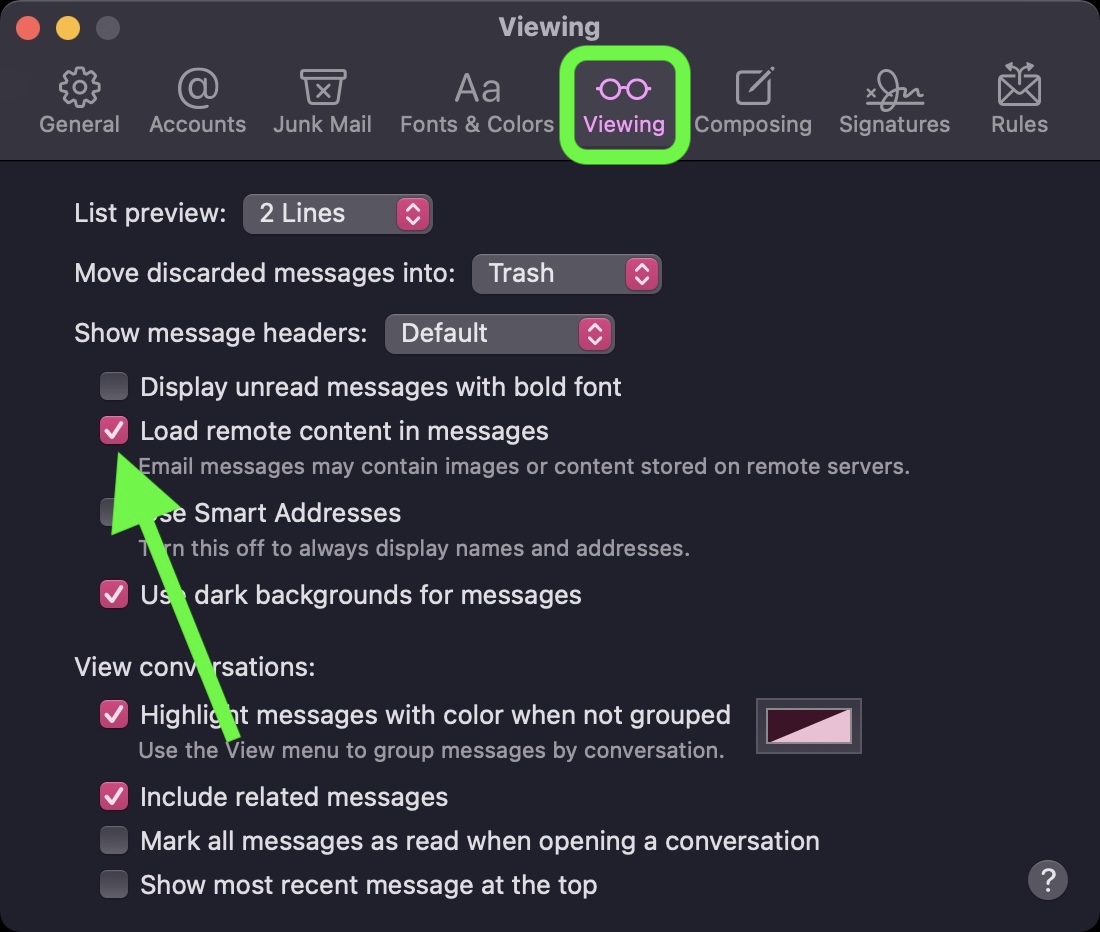
Click the Viewing tab.
Uncheck the box next to Load remote content in messages.
Article Link: How to Prevent Emails From Tracking You in Apple Mail
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.




