
Apple this week shared a support document with details about its new Security Keys for Apple ID feature, available starting with iOS 16.3, iPadOS 16.3, and macOS 13.2. The document provides an overview of the feature and explains how to use it.
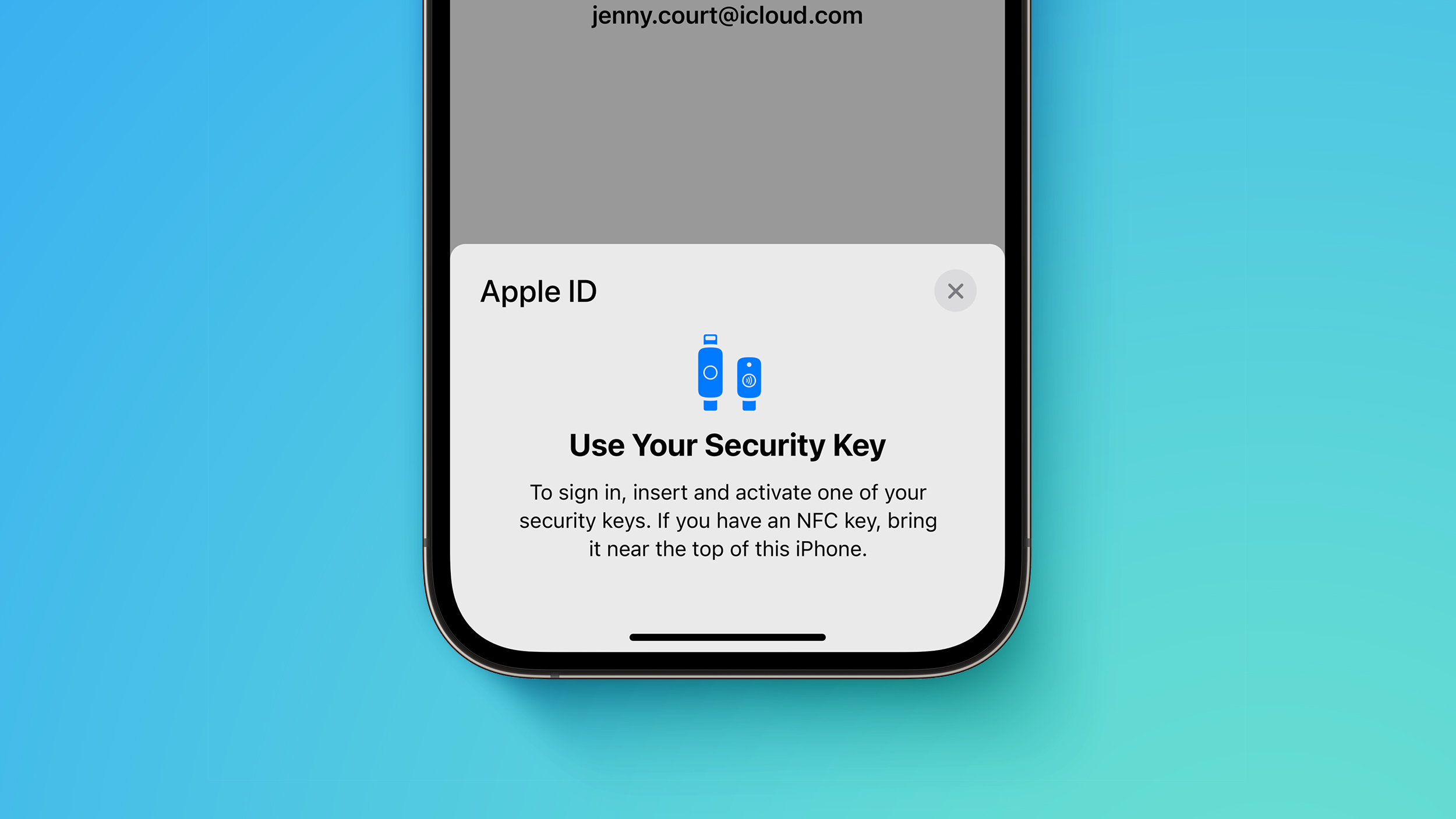
Apple says the optional security feature is designed for individuals who want "extra protection from targeted attacks, such as phishing or social engineering scams." When it is enabled, signing into an Apple ID requires entering your account's password and then using a FIDO Certified security key to complete two-factor authentication, instead of a traditional six-digit verification code from another Apple device.
Those who enable the feature must be very careful not to lose their security keys, as this could result in losing access to your Apple ID account permanently. For this reason, you must set up at least two security keys, with up to six supported in total.
Apple recommends keeping security keys in more than one place. For example, you could hide a key somewhere at home as a backup solution.
"Keep your security keys in a safe place, and consider keeping a security key in more than one place," the document says. "For example, keep one key at home and one key at work. If you're traveling, you might want to leave one of your security keys at home."
To enable Security Keys for Apple ID on an iPhone or iPad, open the Settings app, tap your name, tap "Password & Security," select "Add Security Keys" and follow the on-screen instructions. On the Mac, open the System Settings app, click on your name, click "Password & Security," click "Add" next to "Security Keys," and follow the steps.
Security keys can be removed at any time by repeating the steps outlined above and tapping or clicking on "Remove All Security Keys," at which point your Apple ID reverts to using a six-digit verification code for two-factor authentication.
Many security keys look similar to a USB thumb drive, with some options available with NFC for wireless use and others equipped with Lightning, USB-C, and/or USB-A ports for direct connectivity with iPhones, iPads, and Macs. Apple recommends a few security keys in the document, such as the YubiKey 5Ci with both Lightning and USB-C.
Apple's document provides some other important details, so it is worth reviewing before enabling the feature. For example, you can't sign in to iCloud for Windows when the feature is enabled, and some types of Apple ID accounts are not supported.
Article Link: Apple Explains iOS 16.3's New Security Keys Feature

