
Microsoft's 365 Defender Research Team this morning published details on a new "Powerdir" macOS vulnerability that let an attacker bypass the Transparency, Consent, and Control technology to gain unauthorized access to protected data.
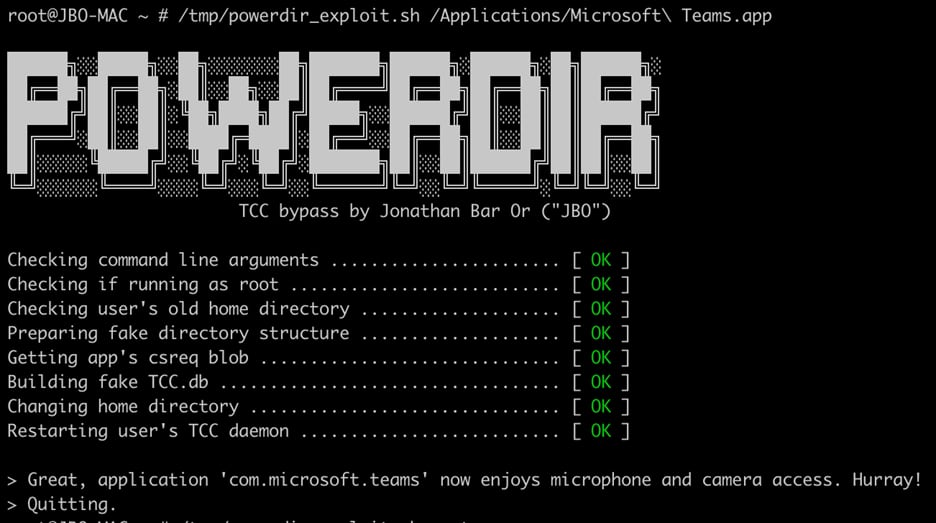
Apple already addressed the CVE-2021-30970 vulnerability in the macOS Monterey 12.1 update that was released in December, so users who have updated to the latest version of Monterey are protected. Those who have not done so should update. Apple in its security release notes for the 12.1 update confirmed the TCC vulnerability and credited Microsoft with its discovery.
According to Microsoft, the "Powerdir" security flaw could allow a fake TCC database to be planted. TCC is a long running macOS function that lets users configure the privacy settings of their apps, and with the fake database, a malicious person could hijack an app installed on a Mac or install their own malicious app, accessing the microphone and camera to obtain sensitive info.
Microsoft has a detailed outline of how the vulnerability works, and the company says that its security researchers continue to "monitor the threat landscape" to discover new vulnerabilities and attacker techniques that affect macOS and other non-Windows devices.
"Software vendors like Apple, security researchers, and the larger security community, need to continuously work together to identify and fix vulnerabilities before attackers can take advantage of them," wrote Microsoft's security team.
Article Link: Microsoft Discovered New 'Powerdir' macOS Vulnerability, Fixed in 12.1 Update




