![]()
With the launch of iOS 16.3 and macOS 13.2 Ventura, Apple added Security Keys for the Apple ID, offering a more robust way to protect your Apple account and everything associated with your Apple account.
A Security Key is a physical device that works with two-factor authentication. Instead of using a code generated by a secondary Apple device for authentication, when you log into your Apple ID on another device after setting up Security Keys, you need to authenticate through a physical key that's actually plugged in to your device.
You can use any FIDO Certified security key to activate the feature, and Apple recommends the YubiKey 5C NFC and the YubiKey 5Ci, two devices sold by
Yubico. Yubico sent me a pair of its security keys so that I could try them out with Apple's Security Key function.
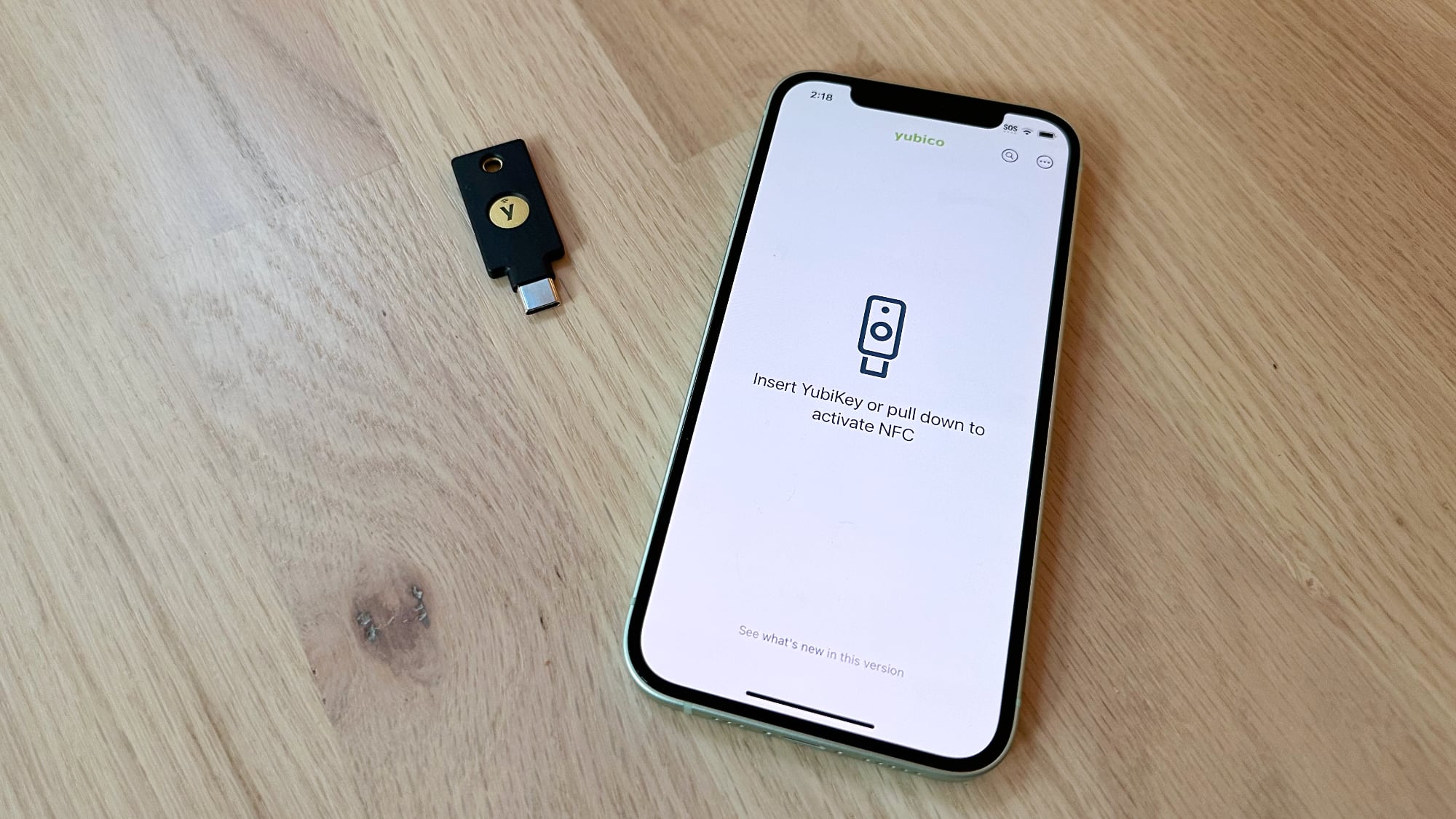
The YubiKey 5Ci has a USB-C connector and a Lightning connector so that it can be plugged into iPhones, iPads, Macs, and other devices that use these connectors, while the YubiKey 5C NFC has a USB-C connector and the ability to interface with NFC-enabled devices.
With Apple eliminating the Lightning port in the iPhone this year and because I don't own any devices without NFC, I opted for the YubiKey 5C NFC for futureproofing, but if you plan to have an iPhone or an iPad with a Lightning port for an extended period of time, the 5Ci might be the better option if you're interested in using Security Keys.
Security Keys can be set up on the iPhone, iPad, or Mac. Note that whatever security key product you pick, you have to have
two, not just one. Apple requires dual security keys for redundancy purposes, and Yubico recommends a pair as well. The reason for this is because if you lose your physical security key, if you don't have another in a safe place, you're going to lose access to your Apple ID. You're going to want to store the Security Keys in two separate locations.
On an iOS device or Mac, Security Keys can be enabled through the Password and Security section of the Settings app. Before you can add a Security Key, you need to sign out of all inactive devices, which includes devices that you have not used in the last 90 days. Older devices won't support Security Keys at all.
I had to go through this process, and I want to note that it didn't quite work properly (which is not the YubiKey's fault). Apple's process signed me out of the unsupported devices or devices I had not logged into, but then the Security Keys setup would not progress. I swapped over to the Mac to continue, and had better luck.
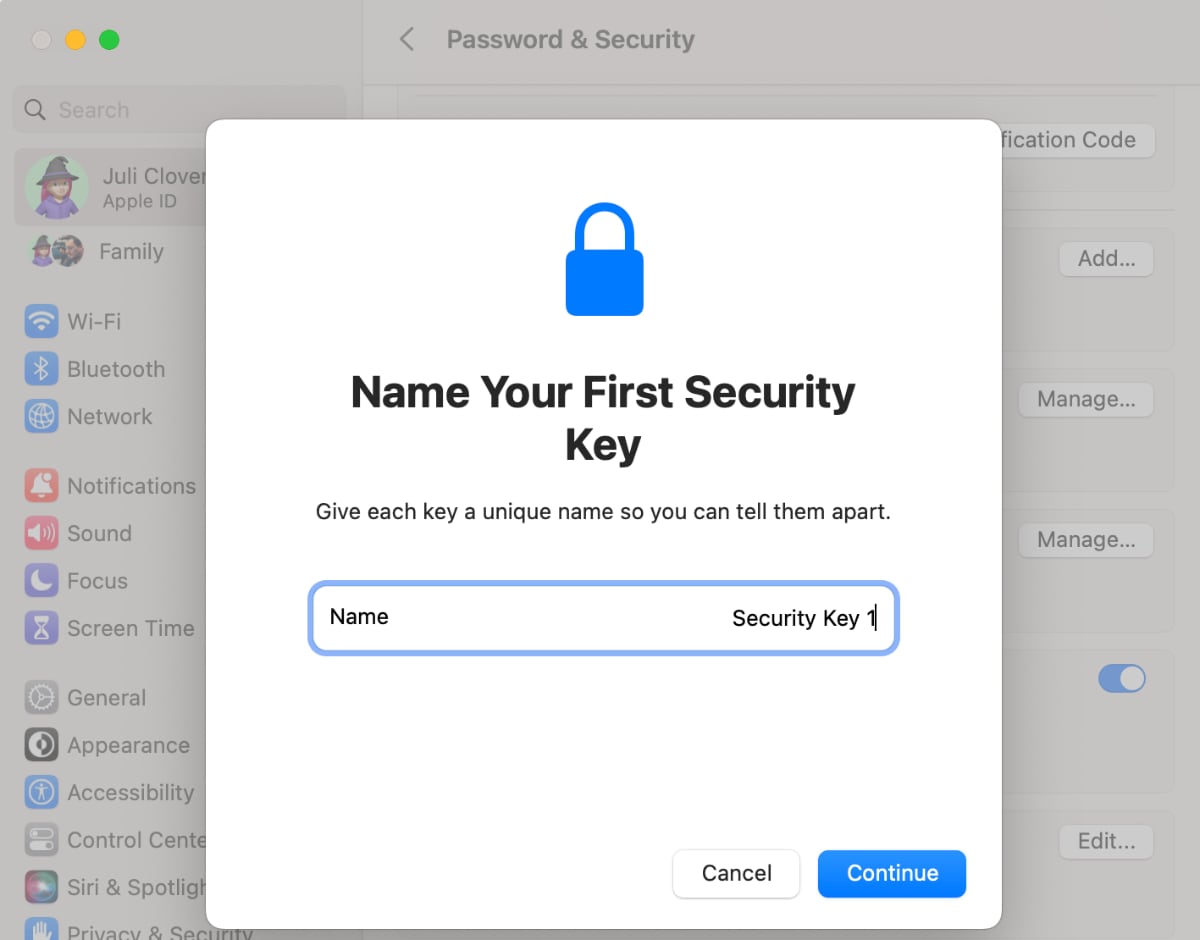
The setup process required me to connect the security key, which I did using USB-C, and then I had to press on the key to get the Mac to recognize it. Apple had me give it a name, and then repeat the process to add the second security key.
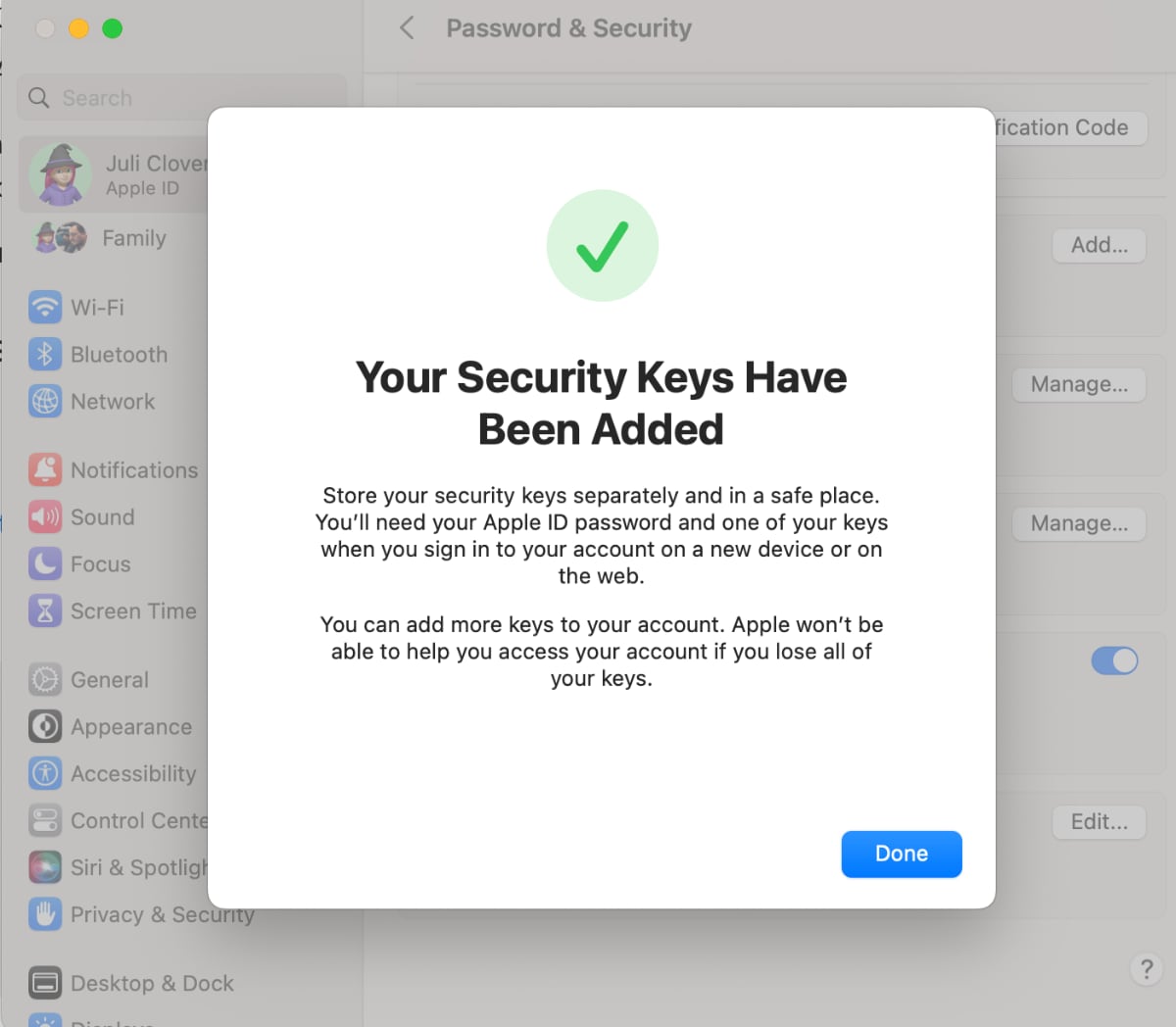
After that, I was instructed to review my list of active devices and choose whether to sign out of any of them. There was an option to stay signed in to everything, which is what I selected. Following the setup process, Apple instructed me to store the keys separately and in a safe place, and clarified that I can add additional keys in the future.
There's also a single line on the bottom of the setup screen that makes it clear Apple has no way to help access an account that is tied to a security key if both keys are lost, a warning that should probably be in bolder text. Apple sends an email about the Security Key setup process, and in both Mac and iOS settings, I can view my connected Security Keys and remove them.
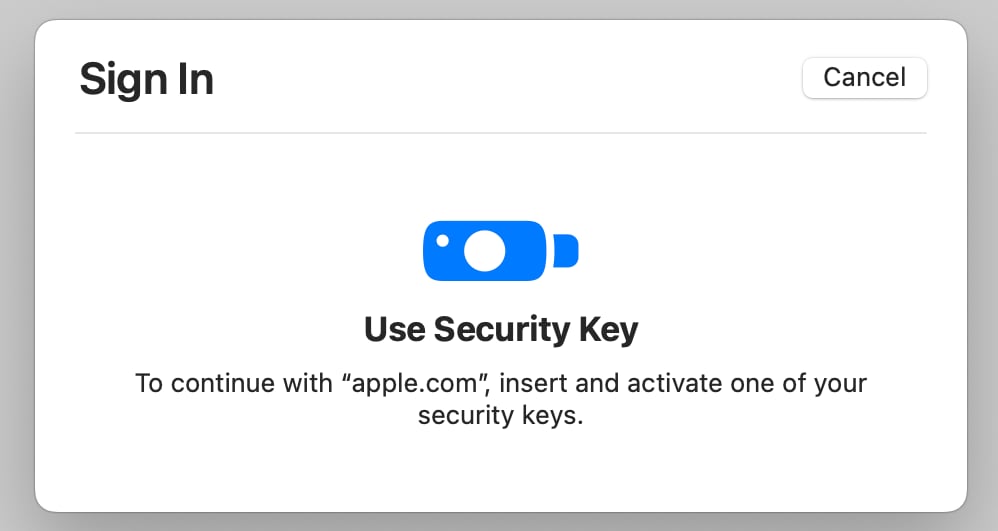
When I attempt to sign into my Apple ID on a device on the Mac, I'm instructed to insert and activate one of my security keys. This process requires inserting the key into a USB-C port and pressing on it to activate it. I receive notifications across all of my devices when a login attempt is made.
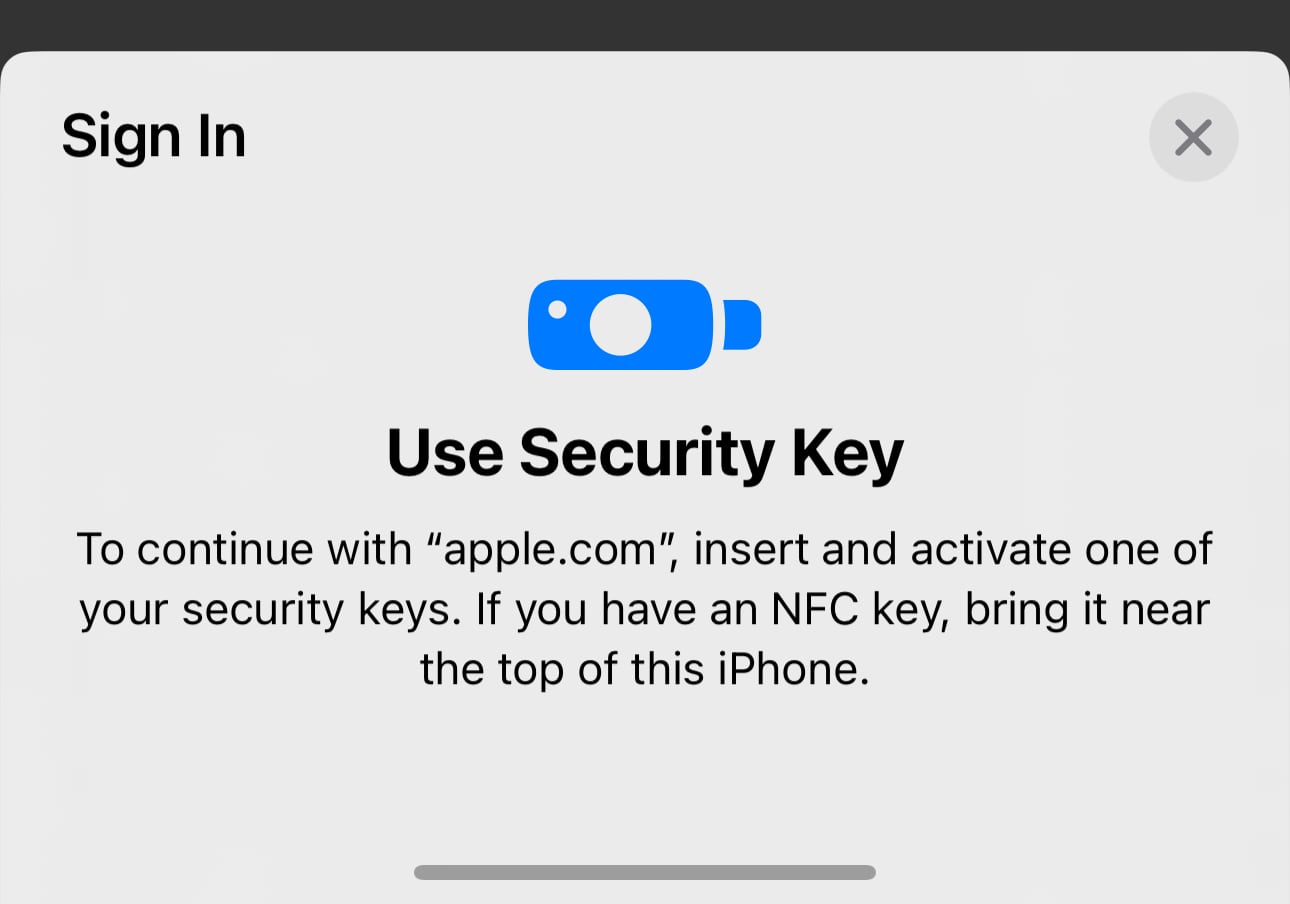
On an iPhone, the login process is similar, but the YubiKey needs to be held near the iPhone's NFC reader (the top of the device) and activated for authentication. In general, it's a simple process on every Mac, iPhone, and iPad I've tested it with. All of my devices are running iOS 16.3 or later or macOS Ventura 13.2 or later, and they all support USB-C or NFC. On devices that are not updated or do not support USB-C/NFC, the process might not be as seamless and could require adapters.
My major worry activating Security Keys is that I'm going to lose one. YubiKeys and other security keys are small, unobtrusive, and easy to lose since they're designed to be kept secret and hidden. The YubiKey has a hole at the top for a keyring, so I'm going to add a keyring to one that will remain in a secure place in my office, and the second will go somewhere safer.
Two-factor authentication with a physical security key is more secure than authentication with a digital code, according to Apple, but it's a little riskier. I can't track my YubiKeys if they're lost, but I can track down all my secondary Apple devices if I should lose one and need it for a code. That said, the authentication process is super easy, and it's even quicker than getting a code from another Apple device.
YubiKeys don't need to charge and seem to be durable so far based on anecdotal reports
from YubiKey users, which is good because I'm also worried about breaking one. Ultimately, I think I may add a third key to my account just for another layer of protection, since there's little chance I'll lose or break three at one time. There's an IP68 water resistance rating so it can hold up to liquid immersion, and it has a storage temperature of -4 °F to 185 °F.
You won't need an app to use a YubiKey for some services (like with an Apple ID or Twitter), but for others, the Yubico Authenticator will need to be installed. The Yubico Authenticator is like Google Authenticator or Authy, generating a code that uses the YubiKey.
I was not able to set up the YubiKey with Instagram because Instagram's authentication process plus the Yubico app simply would not work. The app would not recognize the key, so be aware that there may be some troubleshooting involved. There
are limitations with the YubiKey in terms of supported accounts. It can store up to 25 FIDO2 credentials for password-free logins, two OTP credentials, 32 OATH credentials for one-time passwords (when paired with the Yubico Authenticator), and an unlimited number of U2F credentials. If you have more than 32 accounts where you need one-time passwords, the YubiKey might not be the best solution because it only works with 32 logins.
In addition to an Apple ID, the YubiKey
works with other websites and services with two-factor authentication. Google, Microsoft, 1Password, LastPass, Facebook, Twitter, Instagram, bitcoin wallets, government accounts, and a bunch more are all supported.
Bottom Line
If you're aiming to better secure your Apple ID through physical authentication using the Security Keys feature, the YubiKey series is worth looking at. It offers better protection than you'll get through digital codes, but it is expensive and there are some limitations to be aware of if you want a multi-purpose physical authenticator.
How to Buy
The
YubiKey 5C NFC that I used in this review is priced at $55, and it can be
purchased from the Yubico website. The YubiKey 5Ci with Lightning connector and USB-C connector is
priced at $75.
Article Link:
Review: Yubico's 5C NFC YubiKey Works Well With Apple's Security Keys Feature