This concept has been around for YEARS. This is an attempt to reach out to the masses so they can sell more of them.So this is a Security Researcher who promotes illegal privacy breaches by manufacturing and selling this cable.
What makes him think it will not reach out to the masses?
What makes us think that there may not be already be a mass production of this cable in China?
I'm going to have to start buying my Lightning cables from Apple or a reputable vendor like Satechi or Choetech.
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Security Researcher Develops Lightning Cable With Hidden Chip to Steal Passwords
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
This particular example seems a little sketchy to me, in terms of what they're claiming and what they're showing, but the overall concept is definitely not new and something that not nearly enough people seem to be aware of.This concept has been around for YEARS. This is an attempt to reach out to the masses so they can sell more of them.
state and federal law enforcement, NSA, CIA to name a few....
The device seems too rudimentary for serious use by such agencies. First time it's discovered and you've tipped off a target.
I think a cable with an attached directional high gain antenna would be a bit obvious so that even the fool that gts ahold of one would recognize something is amiss; unless it's labeled "Ignore the antenna used to steal your information".Just buy a directional (high gain) WiFi antenna and you can get over a mile of range. These are sold on Amazon, Newegg and other places.
I take that back, the articles on MacRumors and Vice are frustratingly vague, but their site itself does a much better job of explaining the tech.This particular example seems a little sketchy to me, in terms of what they're claiming and what they're showing, but the overall concept is definitely not new and something that not nearly enough people seem to be aware of.
Kee in mind they’re not claiming that they were able to download data from the device a mile away, just that they were able to “trigger payloads”. That’s a command from the controlling device to the cable. The giant antenna would be attached to the transmitting/attacker machine, not the cable. More gain would help on the receiving side, but wouldn’t be required.I think a cable with an attached directional high gain antenna would be a bit obvious so that even the fool that gts ahold of one would recognize something is amiss; unless it's labeled "Ignore the antenna used to steal your information".
who could be over a mile away
The most ambiguous and pointless statement ever
If I am reading this right, it can just log keystrokes while connected, so just do not enter passwords while connected by a cable.
What is the encryption method used in Bluetooth? AES? 128? 256?Bluetooth keyboards are fine tho? (bluetooth, unlike USB, is encrypted) The cable logs keystrokes only if keystrokes are passed through them.
I’ve always been leafy of Bluetooth devices regarding security.
I went through this debate before I bought my Keychron keyboard.Remember: If an attacker can replace your cable, they could also just replace your entire keyboard with a compromised one…
Logitech, and other have security weaknesses too. The unifying receiver is vulnerable to attack. The newer “Bolt” dongles are supposedly addressing the problem. Will look for the link, and post back…
Never was a fan of Bluetooth, and I always wondered what type of encryption apple used for their keyboards. Anyone know?
Kevin Mitnick has been warning us about this for a while!
A normal-looking Lightning cable that can used to steal data like passwords and send it to a hacker has been developed, Vice reports.

The "OMG Cable" compared to Apple's Lightning to USB cable.
The "OMG Cable" works exactly like a normal Lightning to USB cable and can log keystrokes from connected Mac keyboards, iPads, and iPhones, and then send this data to a bad actor who could be over a mile away. They work by creating a Wi-Fi hotspot that a hacker can connect to, and using a simple web app they can record keystrokes.
The cables also include geofencing features that allow users to trigger or block the device's payloads based on its location, preventing the leakage of payloads or keystrokes from other devices being collected. Other features include the ability to change keyboard mappings and the ability to forge the identity of USB devices.
The cables contain a small implanted chip and are physically the same size as authentic cables, making it extremely difficult to identify a malicious cable. The implant itself apparently takes up around half of the length of a USB-C connector's plastic shell, allowing the cable to continue to operate as normal.
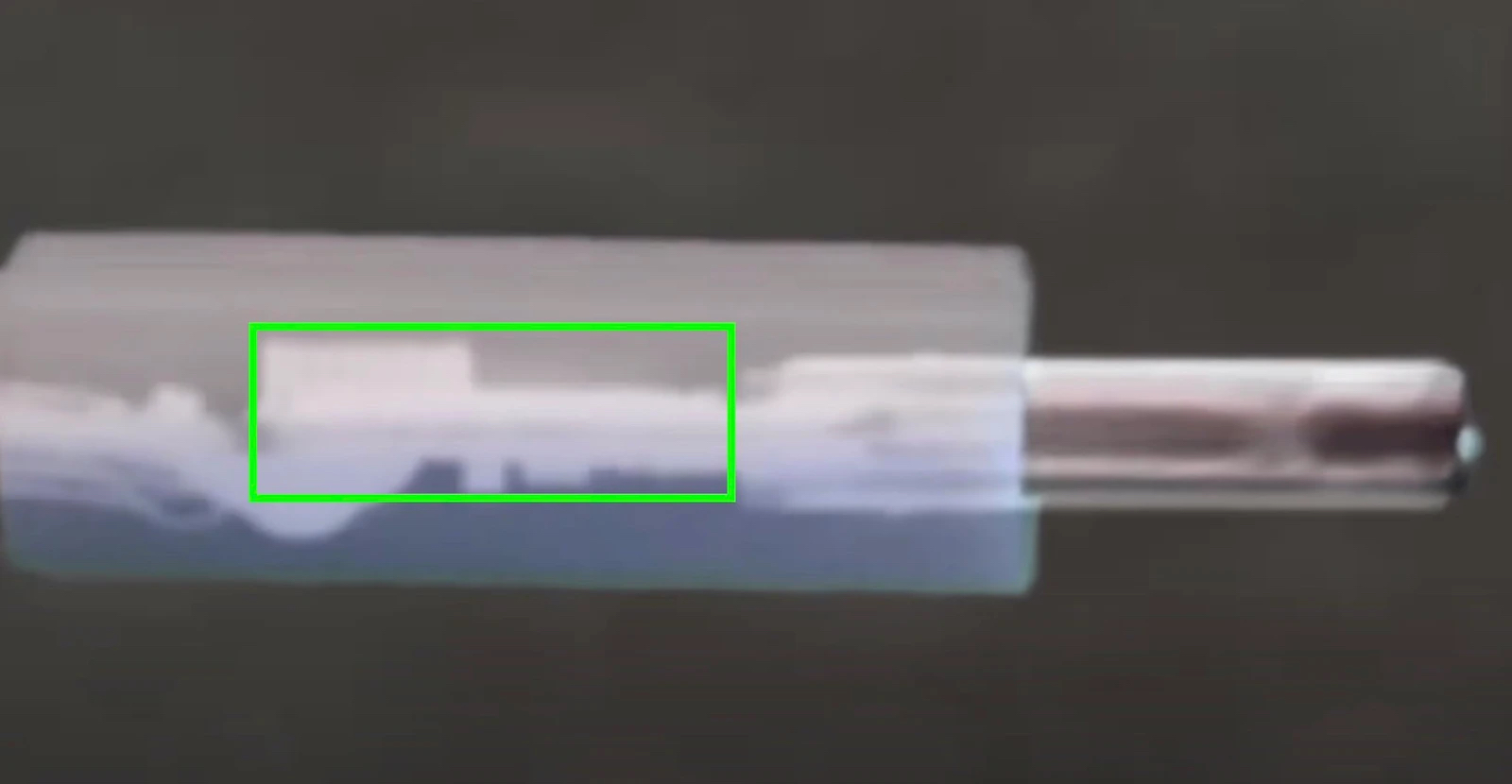
An x-ray view of the implanted chip inside the USB-C end of an OMG Cable.
The cables, made as part of a series of penetration testing tools by the security researcher known as "MG," have now entered mass production to be sold by the cybersecurity vendor Hak5. The cables are available in a number of versions, including Lightning to USB-C, and can visually mimic cables from a range of accessory manufacturers, making them a noteworthy threat to device security.
Article Link: Security Researcher Develops Lightning Cable With Hidden Chip to Steal Passwords
USB Ninja With Kevin Mitnick | How You Can Be Hacked Using a USB Cable - YouTube
Bluetooth - Wikipedia
Bluetooth should probably as safe as other wireless protocols such as WiFi and 5G?What is the encryption method used in Bluetooth? AES? 128? 256?
I’ve always been leafy of Bluetooth devices regarding security.
Not good. Especially now it is entering mass production. In the wrong hands, it can be very dangerous.
I always thought inductive charging was garbage because it was slow and inefficient. Now that would be the first reason for me to charge wirelessly.Wow! That’s very scary. Come up with a port less iPhone already, Apple in 2022.
But very soon, that kind of crud will be built into charging mats. It's easier to integrate there, too. And the biggest problem: All Bluetooth scanner apps are currently extremely inaccurate. And if you then switch to other modulation methods, there are no more control options. Scary!
It’s a pretty solid device, but the attack vector is USB, not the Apple lightning part.
Shortly put, and not new at all: Anything on the USB bus is public to other devices on the USB bus. So this can and has been done for years. Building it into such a small space and adding geofencing is pretty neat though.
The Apple part makes good headlines for sure ;-)
Shortly put, and not new at all: Anything on the USB bus is public to other devices on the USB bus. So this can and has been done for years. Building it into such a small space and adding geofencing is pretty neat though.
The Apple part makes good headlines for sure ;-)
Thank you for that insight!Everyone's fixated on the WiFi range, as if security professionals are only allowed to use off the shelf consumer grade WiFi hardware.
Yes, the WiFi transceiver in your laptop is only able to communicate at relatively short range. But someone trying to hack into a government or corporate entity isn't going to be limited to the same crappy WiFi hardware you're using. With a decent parabolic antenna (hardly unreasonable for someone trying to hack into a valuable target) you can push your range out much farther.
So the point isn't that this cable itself has amazing WiFi range, but that WiFi in general has amazing range if you're willing to use high end hardware on one end of it. It's important for people to be aware that simply physically securing a facility and a short radius around it isn't going to keep people from getting wireless access to a device inside of it.
For all those doubting the range for WiFi google how to make a coffee can antenna or pringle’s can antenna (i.e. a cantenna) and see what kind of range you can get.
It's not the range you can achieve but the ability to establish a duplex connection. They could send a signal on a WiFi band to carry out a function using one - way transmission, but you could do the same thing by hiding the setup in a USB drive. If the want to monitor over a duplex connection both devices need to be in range of the lowest range device, and I doubt they get a mile transmission range in an Apple iPhone cable.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.


