So how exactly are you a "cybersecurity vendor" if you sell garbage like this that exists only to defeat cyber security (and give me another reason to push high-end cables over gas station crap)?
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Security Researcher Develops Lightning Cable With Hidden Chip to Steal Passwords
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
No, there is actually a WiFi radio embedded in the cable itself. The cable has VERY little control over the host.It makes the computer or phone create the network

O.MG Cable - * to USB-C
To get a cable like this, you used to need a million dollar budget or to find a guy named MG at DEFCON. But Hak5 teamed up with MG to allow more people access to this previously clandestine attack hardware. This O.MG Cable is hand made and tailored to look and feel exactly like the cable your...
Don't connect your device to random cables and you'll be fine.
Except that there's an awful lot of people who refuse to pay for good cables, thinking there's no difference between an Apple or an Anker and gas station garbage...
And there's an awful lot of counterfeit Apple goods on Fakebook Marketplace.
The scary part is the mass production… why!? I understand making the cable as a proof of concept, and a “Hey Apple, fix this!” Kinda thing— but who, other than bad actors, will be buying these? Other security researchers? To what end?
This is kind of par for the course for Hak5 products. Relatively expensive product that could be used for legitimate pen testers but for the most part just get bought by kids looking for **** to play around with.So how exactly are you a "cybersecurity vendor" if you sell garbage like this that exists only to defeat cyber security (and give me another reason to push high-end cables over gas station crap)?
The USB cable, which was once thought of as a kind of throwaway device, has now become one of the important legs in device security. I hope Apple makes their own cables more secure and puts up a warning on the screen when using a non-Apple certified cable.
They will sell to "bad actors." 😆So who will they sell to?
You get what you pay for!guess I should pay the $20 to apple instead of the $7 to an ebay seller to keep my info safe? Danggit that sucks!
Where did you read these were "being mass produced?"And why are they mass producing them now? 🤔
The scary part is the mass production… why!? I understand making the cable as a proof of concept, and a “Hey Apple, fix this!” Kinda thing— but who, other than bad actors, will be buying these? Other security researchers? To what end?
Seriously, there's nothing to fix here. It's the way the USB protocol works to talk to a keyboard.
Except that there's an awful lot of people who refuse to pay for good cables, thinking there's no difference between an Apple or an Anker and gas station garbage...
And there's an awful lot of counterfeit Apple goods on Fakebook Marketplace.
So these things run $140 a pop. There's a scary scenario where a bunch of these show up at your local gas station, but let's break that down for a sec.
- The attacker is going to be spending some serious cash
- They need to be within WiFi range of the cable when it's in use to connect to it.
- They're going to sell a ******** of cables hoping that someone uses one to connect a keyboard to their device in order to keylog.
That's all the sudden a pretty high risk/low reward attack. When I say don't use random cables I mean don't use ones you pick up in the parking lot of are lying around at an airport. This is sounding like something fairly targeted,
Yes, there is nothing new here (except miniaturization).For the key logging function you have to be using the cable to hook up between a keyboard and a device so the traffic can be sniffed.
Physical keyloggers have always been possible, even with plain USB or ancient PS/2.
Remember: If an attacker can replace your cable, they could also just replace your entire keyboard with a compromised one, or install a camera to see you type your passwords. Using an (offline) password manager and 2FA can mitigate this.
Last edited:
But many people do use cables that are (or rather that appear to be) "randomly lying around." Imagine you are surveilling a high-value target who uses an iPhone. Put this in his limousine and in his hotel rooms and there's a reasonable chance that one day he might use it to charge his phone.This can only be a thread to device security, if I'm using cables which are randomly lying around or if I buy cables from stores/companies I don't know or trust.
What does Hollywood have to do with this?They will sell to "bad actors." 😆
Edit: Lol, I figured this would be thumbs down and called a lame joke!
Last edited:
Yeah - while it would be foolish to suggest that a fake-USB-accessory attack isn’t a thing, this particular example tickles my BS detector, too. Lots of little things, but what does it for me is the x-ray of the USB-C connector with the embedded microchip... Last I looked all but the most basic USB-C cables had an embedded cable ID chip.I'm going to call BS on this. A powerful compute module with memory, wifi with somehow a one mile range, and location services for geofencing, all in half a USB-C connector?
Still, don’t plug shady USB devices into your computer, folks, the general idea isn’t impossible.
A normal-looking Lightning cable that can used to steal data like passwords and send it to a hacker has been developed, Vice reports.

The "OMG Cable" compared to Apple's Lightning to USB cable.
The "OMG Cable" works exactly like a normal Lightning to USB cable and can log keystrokes from connected Mac keyboards, iPads, and iPhones, and then send this data to a bad actor who could be over a mile away. They work by creating a Wi-Fi hotspot that a hacker can connect to, and using a simple web app they can record keystrokes.
The cables also include geofencing features that allow users to trigger or block the device's payloads based on its location, preventing the leakage of payloads or keystrokes from other devices being collected. Other features include the ability to change keyboard mappings and the ability to forge the identity of USB devices.
The cables contain a small implanted chip and are physically the same size as authentic cables, making it extremely difficult to identify a malicious cable. The implant itself apparently takes up around half of the length of a USB-C connector's plastic shell, allowing the cable to continue to operate as normal.
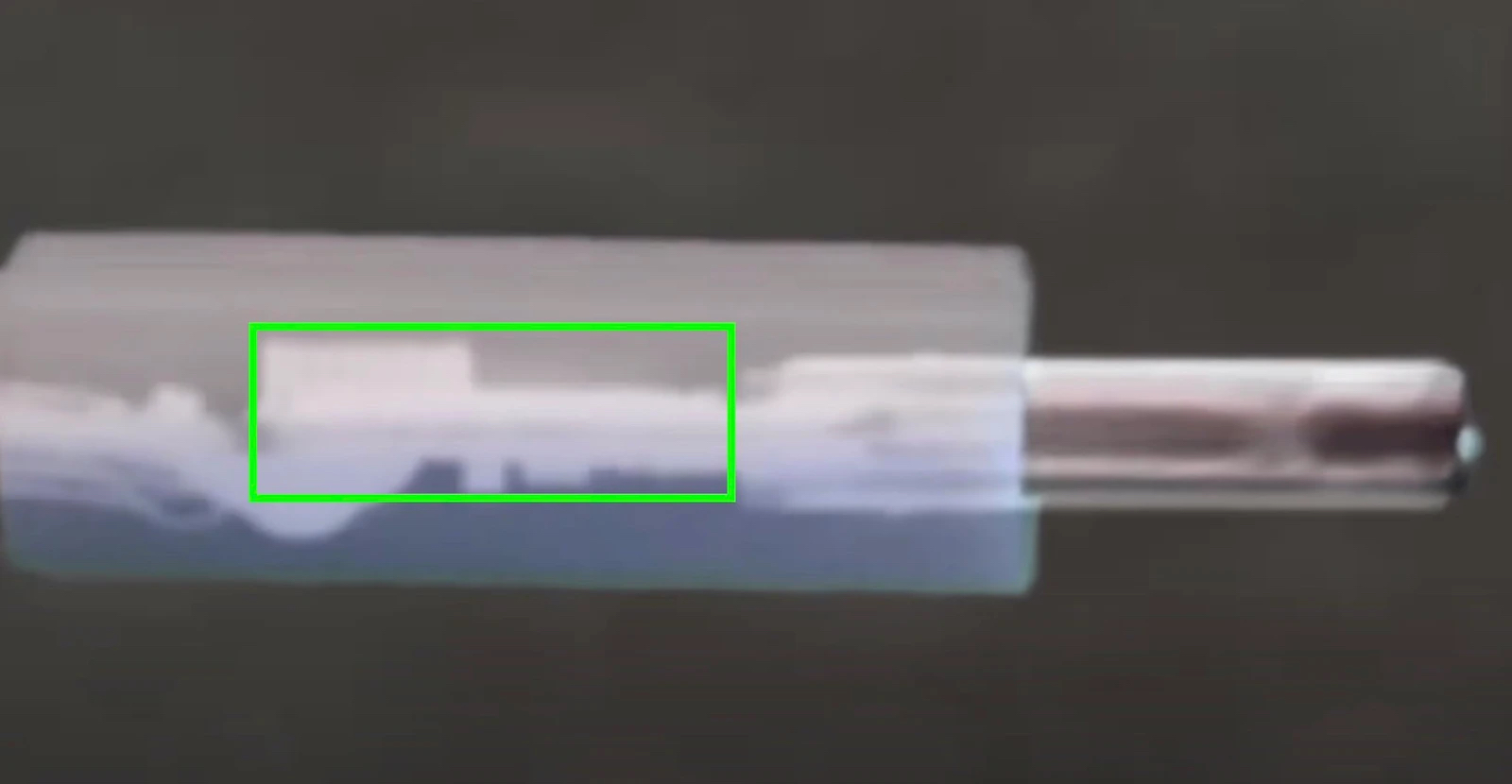
An x-ray view of the implanted chip inside the USB-C end of an OMG Cable.
The cables, made as part of a series of penetration testing tools by the security researcher known as "MG," have now entered mass production to be sold by the cybersecurity vendor Hak5. The cables are available in a number of versions, including Lightning to USB-C, and can visually mimic cables from a range of accessory manufacturers, making them a noteworthy threat to device security.
Article Link: Security Researcher Develops Lightning Cable With Hidden Chip to Steal Passwords
Then, why the hell is this legal to mass produce ? Like what ?
The last paragraph says exactly that:Where did you read these were "being mass produced?"
The cables, made as part of a series of penetration testing tools by the security researcher known as "MG," have now entered mass production to be sold by the cybersecurity vendor Hak5. The cables are available in a number of versions, including Lightning to USB-C, and can visually mimic cables from a range of accessory manufacturers, making them a noteworthy threat to device security.
Charging your phone with this will not steal anything. Your target would have to attach a Magic Keyboard to their iPhone using that cable and happen to manually type passwords while doing that. Not really a promising attack vector …But many people do use cables that are (or rather that appear to be) "randomly lying around." Imagine you are surveilling a high-value target who uses an iPhone. Put this in his limousine and in his hotel rooms and there's a reasonable chance that one day he might use it to charge his phone.
It now seems I'm going to have to start wrapping my lighting cable in tin foil.The last paragraph says exactly that:
The cables, made as part of a series of penetration testing tools by the security researcher known as "MG," have now entered mass production to be sold by the cybersecurity vendor Hak5. The cables are available in a number of versions, including Lightning to USB-C, and can visually mimic cables from a range of accessory manufacturers, making them a noteworthy threat to device security.
The target would need to connect a keyboard to their iPhone, iPad or Mac with this cable, in order to log any passwords. It's a very rare case. Usually people just use the keyboard wireless. Also the hacker needs to get in wifi range which in reality is not miles as we all know.But many people do use cables that are (or rather that appear to be) "randomly lying around." Imagine you are surveilling a high-value target who uses an iPhone. Put this in his limousine and in his hotel rooms and there's a reasonable chance that one day he might use it to charge his phone.
It's a little impressive they managed to get everything to fit in the connector housing, but not that surprising. You're making some assumptions about this, though:I'm going to call BS on this. A powerful compute module with memory, wifi with somehow a one mile range, and location services for geofencing, all in half a USB-C connector?
- It really doesn't have to be a powerful processor at all. Decoding the USB protocol, a WiFi stack, and a webserver can be done pretty easily. We aren't talking about high-end ARM processors or anything.
- The 1 mile wifi range thing sounds impressive, but break it down a bit. They said they were able to trigger a payload at a 1 mile range (not download key logger data or anything). That means they were able to connect in one direction, once. That's a far cry from streaming Netflix a mile away. They could have dropped 99% of the traffic they tried to send, but the one packet got through (once). This REALLY isn't that shocking, especially since the device sending could have been been running a high power transmitter with one hell of an antenna. The device in the cable would have only had to receive.
- Their version of geofencing sounds a lot more basic than what you're thinking. The website mentions it's WiFi based, so it's probably just "when you're in range of an access point with this BSSID". I doubt a whole location DB is being loaded to the device (but it's possible).
These are just some slightly inflated claims about a real device.
What would make them illegal to produce?Then, why the hell is this legal to mass produce ? Like what ?
Patent violations?What would make them illegal to produce?
Exactly this. The article is very misleading as it's making folks assuming that just charging with these cables will steal your information.So there's a lot of scaremongering and assumptions being thrown around here. For the key logging function you have to be using the cable to hook up between a keyboard and a device so the traffic can be sniffed.
In fact, this latest batch is considerably less scary than what MG produced two years ago — those cables worked in the other direction, so they could allow a hacker to remotely take control of your device. Of course, most people would hopefully notice if random keystrokes suddenly started getting tapped into their iPhone or iPad while they were using it (and it wouldn't be possible if the device was locked), but it still offered a slightly more dangerous attack vector than recording keystrokes from the ridiculously small number of people who would use a random cable to connect a wired keyboard to their iPhone or iPad.
I'm going to call BS on this. A powerful compute module with memory, wifi with somehow a one mile range, and location services for geofencing, all in half a USB-C connector?
The geofencing is probably extremely crude - just something looking at IP addresses to approximate where it is.
The wifi range is probably massively exaggerated.
Not sure why you'd think that this is particularly powerful or needs a lot of memory.
What patent? Cables are pretty basic. It's not going to be MFI certified any time soon, but there's been enough independent information available to make clone cables for a long time. This would just fall into the same category as every other clone cable you can find at the gas station.Patent violations?
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.


