What ? How can you ask such a question ? Why isn’t it legal to grow tobacco in your backyard - because it can seriously harm you ?!?! It is the tech they provide that can be used to steal your data and miss lead you. No **** it shouldn’t be legal ?!! Good thing governments are debating pointless App Store payments and fees that don’t bother no one and only benefit large software companies looking to get rich, instead of banning those types of products.What would make them illegal to produce?
Got a tip for us?
Let us know
Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
Security Researcher Develops Lightning Cable With Hidden Chip to Steal Passwords
- Thread starter MacRumors
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Why would eBay sellers sell these at $7 when they would cost far more than a "normal" cable? The most likely use of these is people planting a cable on somebody they know and can monitor nearby (read the article). This has nothing to do with cheap knock-offs vs original Apple cables.guess I should pay the $20 to apple instead of the $7 to an ebay seller to keep my info safe? Danggit that sucks!
It's just a matter of time before the OS can detect these chips in the cables and refuse to work with them.The scariest part of all is what if a batch of cable sold by Apple are cables that include compromised chips? Idk. Right now this looks like a more targeted attack on high-profile personnel, but mass production, especially when the cost is going down enough, could easily mean mass data collection that Apple cannot control.
Please no. In addition to speed issues, it basically renders any device that relies on plugged connection useless, such as a car radio, unless you have a wireless connection that is securely attached; not to mention monitors, storage, keyboards, etc.Wow! That’s very scary. Come up with a port less iPhone already, Apple in 2022.
I assume the chip set and connectors, which is why the prices are so high, but I honestly don't know.What patent? Cables are pretty basic. It's not going to be MFI certified any time soon, but there's been enough independent information available to make clone cables for a long time. This would just fall into the same category as every other clone cable you can find at the gas station.
Last edited:
I could see the FBI and CIA wanting these for their surveillance efforts, however you just can't trust (by definition) that the people who sell these cables don't also have other back door capabilities built into the cables that could then get those organizations in trouble!
It looks like you can still trigger a duckscript payload, so that functionality is still available. But yeah, this is a non-event. BadUSB devices have been available for years that can fake out HID/Ethernet/whatever. The miniaturization is a cute trick, but there's no functional difference between this and what's been available in the past + a plug adapter.Exactly this. The article is very misleading as it's making folks assuming that just charging with these cables will steal your information.
In fact, this latest batch is considerably less scary than what MG produced two years ago — those cables worked in the other direction, so they could allow a hacker to remotely take control of your device. Of course, most people would hopefully notice if random keystrokes suddenly started getting tapped into their iPhone or iPad while they were using it (and it wouldn't be possible if the device was locked), but it still offered a slightly more dangerous attack vector than recording keystrokes from the ridiculously small number of people who would use a random cable to connect a wired keyboard to their iPhone or iPad.
IC organizations don't buy equipment from Hak5 for operations. They have their own devices.I could see the FBI and CIA wanting these for their surveillance efforts, however you just can't trust (by definition) that the people who sell these cables don't also have other back door capabilities built into the cables that could then get those organizations in trouble!
If you think the price for a normal cable is high, you'll go nuts when you see the price for these guys:I assume the chip set and connectors, which is why the prices are so high, but I honestly don't know.

O.MG Cable - * to USB-C
To get a cable like this, you used to need a million dollar budget or to find a guy named MG at DEFCON. But Hak5 teamed up with MG to allow more people access to this previously clandestine attack hardware. This O.MG Cable is hand made and tailored to look and feel exactly like the cable your...
This is supposedly a niche product for security researchers. So what the hail do they need to make it look like a regular Lightning cable?😓 I would imagine they'd want to make it look different for obvious reasons (duh, bad actors getting their meat hooks on 'em).
Yup, it definitely isn't going to have GPS hardware inside.The geofencing is probably extremely crude - just something looking at IP addresses to approximate where it is.
I think it's fair to say he may have gotten a mile, but only under ideal conditions (e.g., direct line-of-sight in an outdoor environment on a clear day). Transmitting logged keystrokes requires almost no bandwidth — we're talking about something that a 40-year-old 300bps modem could handle — so you don't need a very strong Wi-Fi signal, and attenuation is therefore far less of a problem.The wifi range is probably massively exaggerated.
Well, it's pretty telling that Hak5 sells them in its "Mischief Gadgets" category.This is supposedly a niche product for security researchers. So what the hail do they need to make it look like a regular Lightning cable?😓 I would imagine they'd want to make it look different for obvious reasons (duh, bad actors getting their meat hooks on 'em).
Everyone's fixated on the WiFi range, as if security professionals are only allowed to use off the shelf consumer grade WiFi hardware.
Yes, the WiFi transceiver in your laptop is only able to communicate at relatively short range. But someone trying to hack into a government or corporate entity isn't going to be limited to the same crappy WiFi hardware you're using. With a decent parabolic antenna (hardly unreasonable for someone trying to hack into a valuable target) you can push your range out much farther.
So the point isn't that this cable itself has amazing WiFi range, but that WiFi in general has amazing range if you're willing to use high end hardware on one end of it. It's important for people to be aware that simply physically securing a facility and a short radius around it isn't going to keep people from getting wireless access to a device inside of it.
Yes, the WiFi transceiver in your laptop is only able to communicate at relatively short range. But someone trying to hack into a government or corporate entity isn't going to be limited to the same crappy WiFi hardware you're using. With a decent parabolic antenna (hardly unreasonable for someone trying to hack into a valuable target) you can push your range out much farther.
So the point isn't that this cable itself has amazing WiFi range, but that WiFi in general has amazing range if you're willing to use high end hardware on one end of it. It's important for people to be aware that simply physically securing a facility and a short radius around it isn't going to keep people from getting wireless access to a device inside of it.
If you want to be safe from targeted attacks then always buy from stores. Your are a sitting duck when ordering online, because it is possibly to replace the ordered item with a doctored item en route to you.I'll just keep buying Anker cables from Amazon.
Of course this level of paranoia is only needed when you have something really precious to guard, like national secrets or a 7 figure bank account.
The old news is that some guy developed and made these by hand. The new news is that they are now being mass-produced and sold by a security vendor (Hak5).Old news...

Security researcher says this modified Lightning cable can hack your Mac
It looks like a harmless Lightning cable but looks can be deceiving.www.imore.com
Then just get Anker cables from Amazon.I don't know if it is good news or bad news that they'll look just like Apple cables. I never buy Apple lightning cables because they suck.
Nothing new it’s been around for 3yrs now and purchase on eBay originally but blocked so there are channels to essil find it.So who will they sell to?
What is sad about this (even though a security developer) is that I can no longer trust cheaper than Apple options for cables, even if legit. Good for Apple, bad to others...
A normal-looking Lightning cable that can used to steal data like passwords and send it to a hacker has been developed, Vice reports.

The "OMG Cable" compared to Apple's Lightning to USB cable.
The "OMG Cable" works exactly like a normal Lightning to USB cable and can log keystrokes from connected Mac keyboards, iPads, and iPhones, and then send this data to a bad actor who could be over a mile away. They work by creating a Wi-Fi hotspot that a hacker can connect to, and using a simple web app they can record keystrokes.
The cables also include geofencing features that allow users to trigger or block the device's payloads based on its location, preventing the leakage of payloads or keystrokes from other devices being collected. Other features include the ability to change keyboard mappings and the ability to forge the identity of USB devices.
The cables contain a small implanted chip and are physically the same size as authentic cables, making it extremely difficult to identify a malicious cable. The implant itself apparently takes up around half of the length of a USB-C connector's plastic shell, allowing the cable to continue to operate as normal.
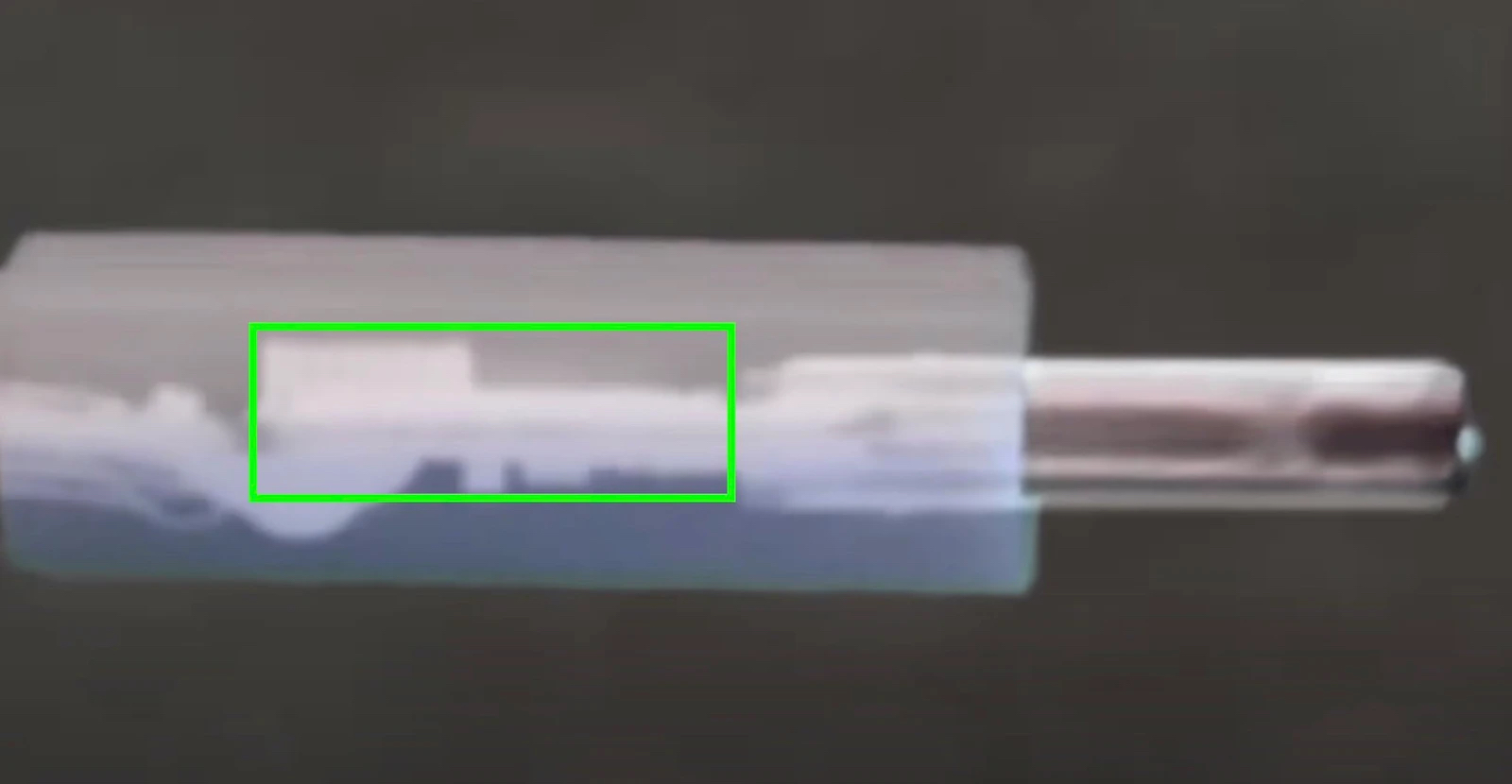
An x-ray view of the implanted chip inside the USB-C end of an OMG Cable.
The cables, made as part of a series of penetration testing tools by the security researcher known as "MG," have now entered mass production to be sold by the cybersecurity vendor Hak5. The cables are available in a number of versions, including Lightning to USB-C, and can visually mimic cables from a range of accessory manufacturers, making them a noteworthy threat to device security.
Article Link: Security Researcher Develops Lightning Cable With Hidden Chip to Steal Passwords
I would think going through extreme lengths to protect your privacy like using burner devices on the Internet and old hardware for your personal data would end up attracting more attention to yourself than just doing things like everyone else does.None of your data is safe unless you have old enough devices from a simpler time, and they’re ineligible for updates. Maybe a Snow Leopard mac or original ipad or something. You just have to stay off the web with it to avoid security shortcomings. Leave your actual computer offline & restricted to your intranet only. Then consider a new device a burner, without any personal data on it, for internet use. Probably the only way forward in the total surveillance 0 privacy era.
We do something a little like this at my company for other reasons, just not so extreme. But i could see it for anyone who prefers a solid sense of security.
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.


